11 Myths About TLS (.PDF Download)
Security issues are persistently front and center when it comes to the internet, and Transport Layer Security (TLS) often is the go-to solution. Nonetheless, myths surround the technology. HCC Embedded CEO Dave Hughes looks to dispel some of these misconceptions.
1. TLS is broken and can’t provide adequate protection against hackers.
Hearing about widely publicized security breaches, you would think that those designing security are incompetent. This is simply not the case. The truth is, there are no known hacks of TLS 1. Rather, these hackers were successful not due to faulty TLS, but because of a lack of software-quality processes.
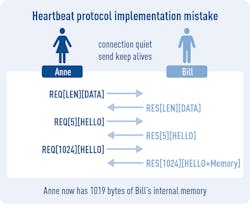
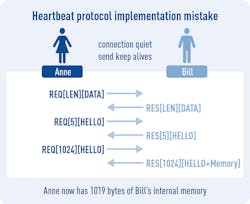
For example, a well-designed static-analysis tool would have detected Apple’s 2017 TLS vulnerability before it was released. And the Heartbleed Bug, which resulted from an implementation defect in some OpenSSL versions, was caused by software that did not check the scope of a protocol variable and then processed it blindly.
Software-quality processes that include unit testing and boundary case analysis/testing would have instantly alerted developers to the issue, and the detection would have been reinforced by other requirements of the lifecycle process.