How to Achieve Low-Cost, Advanced Security For Your Embedded System (.PDF Download)
The availability of low-cost processing power plus ubiquitous connectivity have spurred the rise of the Internet of Things (IoT) and the development of large-scale embedded applications that rely on networks of smart nodes. A smart node in an embedded system typically consists of one or more sensors, a microcontroller, and a wired or wireless connection. Examples are found in almost every IoT application: the electrical grid, the home, the doctor’s office, the factory floor, the automobile are just a few.
As embedded systems proliferate, so have concerns about their security, fueled by well-publicized stories about data breaches, viruses, botnets, trojan horses and the like. The results of an embedded-system security breach can range from inconvenient to life-threatening: video cameras, home routers, cars, drug-delivery systems, and even pacemakers have been hacked.
Embedded system security requires a multifaceted approach
Implementing and maintaining security in an embedded system requires a multi-faceted approach that involves both software and specialized hardware. The task is complicated by the fact that designers are often working under severe cost and size constraints.
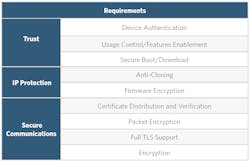
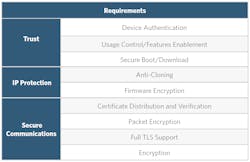
To be considered secure, an IoT system must meet requirements in three categories, as shown in the figure below.
The three key pillars of a secure IoT system. (Image Source: Maxim Integrated)