A recent report by Gartner predicts that there will be 20.4 billion connected Internet of Things (IoT) devices by 2020, with 5.5 million new things getting connected every day. Furthermore, more than half of major new business processes and systems will include an IoT component by 2020.
These numbers are staggering and suggest that standard PC security and anti-virus solutions will not be able to counter future cybersecurity threats on connected IoT devices.
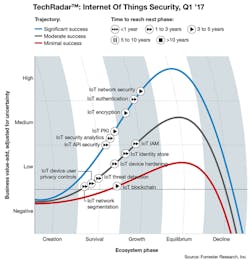
The need for more robust measures to secure IoT embedded devices was confirmed by recent Forrester's TechRadar research that defined the use cases, business value, and outlook for the 13 most relevant and important IoT security technologies. This included core technologies, such as IoT authentication and IoT encryption, in addition to emerging IoT security technologies like IoT threat detection, IoT blockchain, and IoT security analytics (Fig. 1).
1. Forrester Research highlights the outlook for the 13 most relevant and important IoT security technologies (Copyright © 2017, Forrester Research Inc.)
Growing Security Threat
In the last few years, many well-publicized cyberattacks have demonstrated the risks of inadequate IoT security. Perhaps the best known was the “Stuxnet” attack, which targeted industrial programmable logic controllers (PLCs) in an Iranian uranium enrichment facility. Experts believe that Stuxnet destroyed up to 1,000 centrifuges connected via wide-area networks (WANs) to PLC devices running the Windows operating system on standard PC platforms.
Even if you utilize reasonable IoT security measures, your connected gadgets may well be compromised by criminals. Last fall, Dyn—an internet DSN provider—came under an attack that disrupted access to popular websites. The attackers were able to take control of large numbers of internet-connected devices, such as DVRs and cameras. These devices then helped in the attack.
Securing the IoT
Securing the Internet of Things is a tricky business. Take the fact that IoT devices come in every shape, size, and function. This makes traditional end-point security models impractical.
On top of that, by their very nature, IoT devices are resource-constrained in terms of power, performance, and functionality. Many use very customized and non-standard operating systems (remember NANIX, a version of Linux for early wearable devices).
With so many limited resource devices, it’s nearly impossible for network administrators to know what’s going on with all of the devices. Further complicating this issue is that many IoT devices have very long lifecycles and almost no security, i.e., a temperature sensor in a commercial or industrial setting.
Also, many IoT devices can’t be easily patched or upgraded with the latest software due to their original design or limited resources such as memory and process.
Finally, many connected devices use non-standard and legacy communication protocols (think M2M) that aren’t recognized by most security products.
Eight Critical IoT Security Technologies
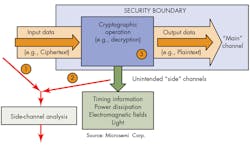
2. Side-channel analysis such as differential power analysis (DPA) or differential electromagnetic analysis (DEMA) is used to extract secret keys from an unprotected processor or FPGA.
As IoT security challenges continue to grow, so too does the need for technologies and processes to address the problems. The following lists eight key technology considerations to improve IoT security:
- Network security: IoT networks are predominately wireless now, as wireless overtook wired global internet traffic back in 2015. This makes security far more challenging than with traditional wired networks due to the variety of emerging RF and wireless communication protocols and standards.
- Authentication: IoT devices must be authenticated by all legitimate users. Methods to achieve such authentication range from static passwords to two-factor authentication, biometrics, and digital certificates. Unique to IoT is that devices (e.g., embedded sensors) will need to authenticate other devices.
- Encryption: Encryption will be needed to prevent unauthorized access to data and devices. This will be difficult to ensure due to the variety of IoT devices and hardware profiles. Encryption must be part of a complete security management process.
- Security-side-channel attacks: Even with adequate encryption and authentication, another threat is possible, namely, side-channel attacks. Such attacks focus less on information transfer and more on how that information is being presented. Side-channel attacks (SCAs) collect operational characteristics—execution time, power consumers, electromagnetic emanation of the design to retrieve keys, and fault insertion—to gain other insights into the design (Fig. 2).
- Security analytics and threat prediction: Not only must security-related data be monitored and controlled, it must also be used to predict future threats. It has to complement traditional approaches that look for activities that fall outside of an established policy. Prediction will require new algorithms and the application of artificial intelligence to access non-traditional attack strategies.
- Interface protection: Most hardware and software designers access devices via an application programming interface (API). Securing these interfaces requires the ability to authenticate and authorize devices that need to exchange data (hopefully encrypted). Only authorized devices, developers, and applications should be capable of communication between secure devices.
- Delivery mechanisms: Continuous updates and patches will be needed to deal with the constantly changing tactics of cyberattackers. This will require expertise in patches, essentially fixing gaps in critical software on the fly.
- System development: IoT security requires an end-to-end approach in the network design. Also, security should be a full product-lifecycle development activity, which becomes difficult if the product is only a smart sensor. Security is still an afterthought for most designers, something that follows the implementation (not design) phase. It’s critical that both hardware and software be considered in these secure systems.
Summary
The rapid growth of IoT devices and the challenges posed by wireless connectivity among these devices necessitates an expanded focus on cybersecurity. The eight key critical IoT security technologies presented here are a combination of traditional and newer methods and tools that work to truly secure the IoT.
About the Author
John Blyler
John Blyler has more than 18 years of technical experience in systems engineering and program management. His systems engineering (hardware and software) background encompasses industrial (GenRad Corp, Wacker Siltronics, Westinghouse, Grumman and Rockwell Intern.), government R&D (DoD-China Lake) and university (Idaho State Univ, Portland State Univ, and Oregon State Univ) environments. John is currently the senior technology editor for Penton Media’s Wireless Systems Design (WSD) magazine. He is also the executive editor for the WSD Update e-Newsletter.
Mr. Blyler has co-authored an IEEE Press (1998) book on computer systems engineering entitled: ""What's Size Got To Do With It: Understanding Computer Systems."" Until just recently, he wrote a regular column for the IEEE I&M magazine. John continues to develop and teach web-based, graduate-level systems engineering courses on a part-time basis for Portland State University.
John holds a BS in Engineering Physics from Oregon State University (1982) and an MS in Electronic Engineering from California State University, Northridge (1991).