Download this article in PDF format.
The rapid rise in cybercrime, along with the well-documented costs to enterprises that manage the fallout of data breaches, has pushed the issue of network data security to the forefront as a strategic business issue. The Ponemon Institute estimates that the annual cost of cybercrime to an organization can be as high as $65 million USD.1 The deluge of data traffic hitting networks worldwide, including the mass migration of enterprise and personal data and workloads to the cloud, is the primary flashpoint for this issue.
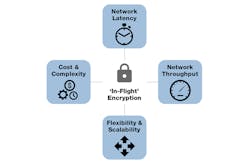
The privacy of data is most exposed as it transits optical-fiber links between data centers, enterprise, and central office sites that serve as the sources and end points of these services—the point at which extensive physical security measures commonly in place at these sites are no longer effective. It’s no surprise, then, that “in-flight” network layer encryption is quickly becoming a main (in some cases, mandatory) requirement for the optical transport equipment servicing these networks (Fig. 1). Key factors include:
- Complexity and cost: The complexity and cost of implementing and managing encryption end-to-end in the network increases at higher layers in the network stack.
- Network latency: Securing traffic “in-flight” must not compromise what is currently defined as an acceptable user experience for on-demand, mission-critical cloud-based services.
- Network throughput/utilization: Given the CAPEX and OPEX costs associated with bringing new network capacity online, any tradeoffs in network efficiency resulting from encryption must be weighed carefully.
- Flexibility and scalability: Operators need to carefully evaluate any trade-offs associated with the compatibility and impact of encryption techniques on the large diversity of clients, rates, services and network technology and architecture choices in play today.
Encrypting data at Layer 1 (L1) with Optical Transport Network (OTN) provides network operators with a compelling option for securing traffic in OTNs effectively, efficiently, and flexibly without trading off service performance or fiber efficiency.
1. Operators must weigh four key factors when evaluating network-layer encryption technology options.
A Closer Look at OTN
OTN is the de facto transport protocol for next-generation 100G+ metro and Core Optical Transport networks worldwide. Defined by the ITU G.709 standard, OTN is a multi-service, multi-rate convergence layer. It’s capable of supporting multiplexing, transport, and switching of virtually all client types and protocols, from Ethernet, SONET/SDH, to data-center-focused constant-bit-rate (CBR) clients such as Fibre Channel, spanning 1- to 100-Gb/s data rates.
As such, unlike alternative Layer 2 (L2) and Layer 3 (L3) encryption techniques, OTN encryption inherently provides network operators with a single encryption solution that addresses all client types and protocols end-to-end within optical transport networks. Agnostic to the client type, protocol, or rate, OTN encryption encrypts the OTN transport payload frame, known as an OPUk. Existing reserved bytes within the overhead of the OTN frame carry the authentication tag.
The encryption block cipher and authentication modes used vary and are implementation-specific. However, implementing strong Advanced Encryption Standard 256-bit (AES-256) block cipher with support for both GCM and CTR authentication modes is possible and available in select OTN processing silicon solutions on the market today.
Introducing network layer encryption doesn’t come without tradeoffs in cost, power, and complexity. In all cases, though, the incremental cost and power of encrypting traffic is hardware-implementation-specific. At the OTN layer, typical incremental processing requirements to encrypt and decrypt OPUk payload and insert/read authentication fields can be considered minimal and lower than the requirements to do so at L2 and L3, since limited buffering and complex filtering hardware is required. In addition, the complexity of managing secure transport at L1 end-to-end can be considered akin to L2, and significantly less complex than doing so at the IP layer.
All network-layer encryption techniques inherently add to network latency. The magnitude is a function of encrypted payload frame size as well as the parameters of the implementation, including hardware architecture, cipher block size and key length, cipher mode, and authentication mode. OTN as a transport protocol is inherently low latency, and encryption at the OTN layer is no different.
Sub-180-ns latencies are achievable today for all OPUk frame sizes using an AES-256 block cipher. Incremental latencies of this magnitude leave plenty of margin in the available end-to-end budget for common mission-critical cloud-based services. Amazon AWS EC2 service, as an example, aims for latencies of 2 ms or less to ensure acceptable user experience – encrypting the optical layer with OTN absorbs only a very small piece of the available margin for this type of cloud service.2
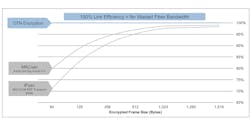
2. OTN encryption delivers 100% link efficiency regardless of the underlying client type or frame size of packet-based traffic.
As neither the underlying payload nor the existing OTN frame are padded or extended in any way to facilitate the encryption or authentication, securing the optical layer with OTN encryption doesn’t come at the expense of precious fiber bandwidth. OTN encryption offers 100% throughput regardless of the underlying client type or frame size of packet-based traffic, whereas L2 or L3 implementations reduce the available optical fiber bandwidth by greater than 20% (Fig. 2).
The Flexibility Factor
Securing the optical layer with OTN encryption also delivers maximum deployment flexibility—it can be rolled into existing L1 transport networks and service models in play today, and provides the means to support emerging network architectures and new, high-value, revenue-generating services. Encrypted OTN traffic can transparently traverse node-to-node through existing OTN-based transport networks. Encryption/decryption is only required at the source and destination in the network.
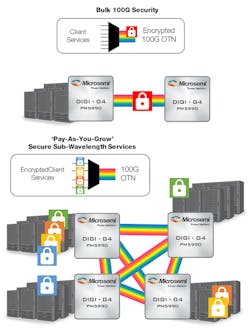
Furthermore, encrypting traffic at the OTN layer mirrors the scalability and flexibility inherent to the G.709 standard—traffic can be encrypted from 1.25 Gb/s up to 100 Gb/s and before or after multiplexing into higher-rate 100G OTN signals. This degree of configurability enables network operators to augment traditional “bulk” or wavelength granularity encrypted service models with new “pay-as-you-grow”’ or “sub-wavelength”’ encrypted transport services, where traffic is secured at granularity of the client services (Fig. 3). The latter model allows enterprise customers to start small and grow their secure leased line needs over time, minimizing the barrier to adoption for new high-value secure transport services.
3. Network operators can augment traditional “bulk” or wavelength-granularity encrypted service models with new “pay-as-you-grow” encrypted transport services.
On top of that, securing traffic at sub-wavelength granularity aligns well with the 100G metro switching network architectures of the future. L1 OTN switching and converged Packet Optical Transport (P-OTP) network equipment are leveraged as a means to aggregate and switch sub-wavelength traffic to ensure the most efficient use of costly 100G optical infrastructure. In this case, secure sub-wavelength traffic flows, possibly from different customers, can be routed through the network independently without the need to decrypt traffic (and therefore compromise data integrity) at each node. This delivers end-to-end security of individual traffic sources at no cost to network efficiency or performance.
Sub-wavelength OTN encryption isn’t limited to deployment in L1 OTN switching network configurations. Such flexibility is especially important given that service provider networks today are a mix of point-to-point WDM and L1 switched architectures.
For instance, sub-wavelength encryption could be deployed in 100G Muxponders at the edge of the network to aggregate and encrypt lower-rate traffic onto higher-rate unencrypted 100G wavelengths. As this traffic transitions to the Metro Core and Backbone networks, predominantly based on mesh-based OTN switching networks, individual sub-wavelength encrypted clients can continue to traverse networks independently. And they wouldn’t need to decrypt higher-rate wavelengths and in turn compromise the security of sub-wavelength traffic. As the network evolves over time, pushing L1 switching closer to the Metro Edge, the encryption model doesn’t need to change.
Conclusion
The need to encrypt data and communications in public and private optical transport networks is strong and growing. Securing the optical layer with OTN encryption provides a compelling solution to this problem. OTN encryption offers a low-latency, service- and protocol-agnostic implementation that makes efficient use of network bandwidth—a critical requirement for network operators fighting to stay ahead of the deluge of data.
Moreover, continued market innovation in OTN processing silicon is enabling network operators to support flexible and scalable network and service models, including L1 OTN switched or point-to-point WDM. This not only allows network operators to enhance existing offerings, but also pursue new revenue and profit generating-services to differentiate themselves in the market, without the need to deploy corresponding Greenfield networks.
References:
1. “2015 Cost of Cyber Crime Study: Global,” Ponemon Institute, Oct 2015.
2. Amazon AWS Elastic Cloud Compute (EC2) 2014-10-02.