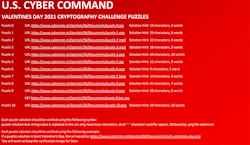
A few people, likely with a sense of humor, over at the U.S. Cyber Command decided to post via Twitter a series of somewhat cryptic Valentine’s Day cards (Fig. 1). Some are even audio offerings. Of course, you probably don’t want to take these at face value—although you could.
On the plus side, the link page provides a hint to the solutions in the form of a character and word count. I looked and listened to them all and have yet to come up with any of the answers. These definitely aren’t straightforward puzzles.
Part of this challenge doesn’t merely involve figuring out the solution; it’s also uncovering how the solution is encoded. Puzzle 6 (Fig. 2) might look straightforward, at least at the start. Four colors are used to make the Xs in this visual Valentine’s Day greeting. Each X can encode four bits based on the colors; two bits for four colors and two-bit pairs per X. Two Xs would be eight bits for a single character if we use something like ASCII or EBCDIC. Of course, that would be too simple. Plus, there’s the issue of whether these digits are grouped in some fashion.
On the other hand, there are dozens of other ways to encode information in this file; the “I Luv U” text and Xs are simply a distraction. The file itself could be implemented using various forms of steganography (hiding a secret message inside of, or on top of, something that’s not secret). An image could be hidden visually. It could be exposed by applying a filter in an image-editing program. Another alternative would be to look at the binary dump of the file. Additional information can be included in the file that would not affect the visual presentation.
I thought the two audio offerings were intriguing. Just thinking about how the information was encoded gave me conniptions. It might be the tones and/or duration. Some notes may have significance while others are superfluous.
If you figure any of these out give me a better hint.
I also found the discussions on various boards like Slashdot and Reddit to be interesting. There were very few useful comments about how to solve the problems and no answers. Must be like the magician’s code: Don’t reveal the magic to a non-magician. You have to figure it out yourself.
Actually, more comments ragged on the relationship with the NSA (National Security Agency) as well as the propriety of the organizations. I would skip these discussions if you’re trying to figure out the puzzles.
The difficulty in solving these puzzles should highlight the challenges of dealing with encryption, authentication, viruses, and other attacks that we deal with all of the time because we’re using or developing computer-based solutions. Although finding the solution to one or more puzzles may be challenging, the mechanism and solution are likely to be simple once the methodology is known. The problem with a simple solution is that it would not be very secure in the long term.
I was hoping that they would have given an example, but you can find plenty of those on the internet. The trick with the Valentine’s Day puzzles is applying any of that knowledge to extract the answers.
I suspect that most will view these puzzles in the same manner as they view encryption and authentication used to secure the IoT. It’s a black box that does magic, and we have to trust in the magicians that it does what they say it will.
So, happy Valentine’s Day from the U.S. Cyber Command. We hope your head doesn’t hurt too much.