How to Achieve Low-Cost, Advanced Security For Your Embedded System
Download this article in PDF format.
The availability of low-cost processing power plus ubiquitous connectivity have spurred the rise of the Internet of Things (IoT) and the development of large-scale embedded applications that rely on networks of smart nodes. A smart node in an embedded system typically consists of one or more sensors, a microcontroller, and a wired or wireless connection. Examples are found in almost every IoT application: the electrical grid, the home, the doctor’s office, the factory floor, the automobile are just a few.
As embedded systems proliferate, so have concerns about their security, fueled by well-publicized stories about data breaches, viruses, botnets, trojan horses and the like. The results of an embedded-system security breach can range from inconvenient to life-threatening: video cameras, home routers, cars, drug-delivery systems, and even pacemakers have been hacked.
Sponsored Resources:
- DeepCover® Embedded Security Solution Guide
- Isolate Software Execution with a DeepCover Security Framework
- How Unclonable, Turnkey Embedded Security Protects Designs from the Ground Up
Embedded system security requires a multifaceted approach
Implementing and maintaining security in an embedded system requires a multi-faceted approach that involves both software and specialized hardware. The task is complicated by the fact that designers are often working under severe cost and size constraints.
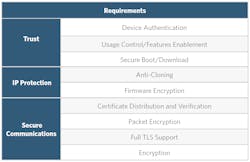
To be considered secure, an IoT system must meet requirements in three categories, as shown in the figure below.
The three key pillars of a secure IoT system. (Image Source: Maxim Integrated)
One key component is the ability to isolate secure functions from externally-accessible ones so that non-secure applications can’t modify secure resources. The standard approach quarantines secure functions in a “trusted zone”. The OS isolation software, typically called a hypervisor, uses a hardware memory management unit (MMU) to set up distinct and separate software "boxes" or "containers". The hypervisor also restricts access to hardware blocks that might be targeted for attack, such as the cryptographic engines, the reset circuitry, protection circuitry, and real-time clock.
The hypervisor defines the resources to be allocated to each of the software boxes and sets up communication channels between them. All software boxes must be executed within their own boundaries and cannot exceed their assigned privileges. The hypervisor then controls access to the different blocks according to the allowed channels and rejects actions that violate the defined rules. Examples of rejected actions might include attempts to obtain additional resources or perform an illegal or unauthorized access.
DeepCover Security Framework Architecture: protection for embedded systems
The MMU is a standard feature in high-end microcontrollers (MCUs) such as the Arm® Cortex®-A family of cores. These cores are widely used in performance-intensive applications running a full-featured OS such as Linux or Android, such as set-top boxes or enterprise networking equipment.
Many embedded systems don’t need a Cortex-A level of performance for remote nodes, so designers use cost-effective MCUs such as Arm’s Cortex®-M that include a Memory Protection Unit (MPU) in place of an MMU; the simpler architecture reduces the die size and lowers the cost.
This isn’t an issue in non-secure applications because the embedded software can be treated as a single monolithic piece of code where all applications share the same resources and privileges. In a large and complex embedded application with security requirements, the Cortex-M’s lack of an MMU makes it difficult to ensure that there is no interaction between the secure and non-secure elements. Since the code is only as secure as its least secure portion, additional help is needed to help meet all the requirements for robust security.
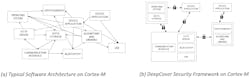
The DeepCover Security Framework (DSF) from Maxim Integrated solves this problem. The DSF builds on the Arm Mbed™ platform, the software framework proposed by Arm for the IoT market, and transforms the chaotic situation in the figure below (left side) into the orderly arrangement shown in the right side. The framework includes a hypervisor that isolates the different software boxes, guarantees their integrity and authenticity, and controls communication between them.
In a typical embedded system, there is no separation between secure and non-secure elements. The DSF security framework provides much-needed isolation. (Image Source: Maxim Integrated)
The DSF provides a system-level approach to security. A secure bootloader provides the root of trust by verifying controlling the origin and authenticity of any software on the platform. A secure box provides services for functions such as key management, cryptography, secure memory management, and secure code update.
The Mbed-based solution includes device drivers, libraries, a real-time operating system (RTOS) environment, as well as complete, ready-to-build application templates. DSF can also be integrated into other common frameworks such as FreeRTOS™.
Hardware-based designs take security to the next level
A purely software-based approach is only as secure as the underlying operating system (OS). A complex OS accumulates many patches over time; any one can potentially be a point of entry and allow an attacker to compromise the encryption code or modify private keys.
Hardware-based security is a more robust approach than a pure software solution because it provides a “root of trust” – a foundation that cannot be modified because it’s physically contained within a device. A private key stored in secure ROM, for example, cannot be altered or read by an attacker; a secure MCU can then use this key to verify and authenticate the signature of any application software.
An embedded system adds another complication. Since it often includes many remote nodes, attackers can attach a fake node to the network and attempt to pass it off as genuine. If they’re successful, the node can be used to gain unauthorized access. The system therefore requires endpoint security that allows the network server to authenticate a remote node.
For endpoint security, a secure MCU may be too expensive, require the development of complex firmware, or consume too much power for an embedded node that relies on battery power. A standalone secure authenticator device allows a designer to add security to an embedded system without becoming a cryptographic expert, or even programming the device. The embedded MCU merely needs to transfer an encrypted message from the network to the secure authenticator, which will use its internal cryptographic engine and stored keys to determine whether the information is genuine.
As well as protecting against attack, a secure authenticator can protect against counterfeiting by ensuring that only genuine parts are used in a system.
There’s yet another complication in an embedded system, even if all the nodes are fully-equipped with secure authenticators. If an attacker can’t spoof the network into accepting a fake node as real, they might be able to gain access to the network by stealing or buying a node and carrying out an invasive physical attack on the secure MCU or authenticator: de-capsulating the device and probing memory locations directly to learn private information.
In response, many secure MCUs and authenticators incorporate an active die shield: a conductive mesh that surrounds the integrated circuit to protect against decapsulation. The device monitors the shield for interruptions or short circuits; if it detects tampering, the part can take action such as, for example, zeroing out sensitive locations.
A “physically unclonable function” (PUF) provides state-of-the-art protection for private keys. A PUF relies on the fact that although semiconductor manufacturing is a highly-precise operation with tight control of process parameters, each device still has random uncontrollable analog variations in its physical microstructure. A PUF authenticator uses these variations to formulate a key based on its unique individual characteristics. The key is repeatable over temperature, voltage, and IC operating life, but any invasive physical attack such as probing modifies the underlying variables and changes the key value, rendering it useless.
Examples of Maxim Secure Authenticators
Maxim Integrated has several secure authenticators in volume production that offer inexpensive alternatives to an MCU upgrade.
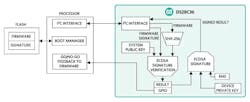
The DS28C36 interfaces to the host processor via IIC to provides ECDSA signature verification. (Image Source: Maxim Integrated)
Maxim’s DS28C36 provides FIPS-186-compliant ECDSA signature generation and verification using a hardware-implemented crypto-engine and a core set of tools derived from asymmetric (ECC-P256) and symmetric (SHA-256) security functions. The part incorporates a die shield, along with other security functions: a FIPS/NIST true random number generator (TRNG); 8 KB of secured EEPROM; a 17-bit decrement-only counter for limited-use applications; two configurable general-purpose input/output (GPIO) pins; and a unique 64-bit ROM identification number (ROM ID) that serves as the device’s private key.
The figure above illustrates how the DS28C36 is used in a secure boot or secure download application. The device uses the system public key to verify the firmware and then the signature of the file download; it then provides a go/no go indication to the host processor either on the GPIO pins or, for added security, via an ECDSA-signed result using the private device key. Following this sequence, the firmware is verified and can proceed to run.
Maxim implements the PUF method via its patented ChipDNA™ technology. For greater security, a ChipDNA device generates the unique PUF key variable only when it's needed for a cryptographic operation. After the operation is complete, the device immediately deletes the variable so it’s not available for an attacker to access.
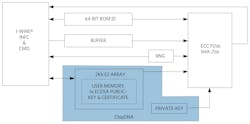
A simplified block diagram of the DS28E28 (Image Source: Maxim Integrated)
Chip DNA is included in several of Maxim's security products, such as the DS28E38 (block diagram show above) is a secure authenticator that uses ChipDNA to encrypt all data stored in the device, plus generate a private key for ECDSA public-key encryption. The part also includes a die shield, a 17-bit decrement-only counter, and 2Kbits of EEPROM for user data, keys, control registers, or certificates.
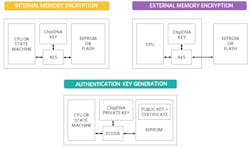
The figure below illustrates several of the use cases for the DS28E38: internal and external memory encryption, and authentication key generation.
Potential use cases for the DS28E38. (Image Source: Maxim Integrated)
Conclusion
Embedded systems often have constraints that make adding robust security difficult. Rather than compromise on quality, which may open up the entire system to attack, several options are available that provide advanced protection for an embedded system while still allowing designers to meet cost and size goals.
Maxim Integrated is a leader in this area and has both software and hardware solutions available.
Sponsored Resources:
- DeepCover® Embedded Security Solution Guide
- Isolate Software Execution with a DeepCover Security Framework
- How Unclonable, Turnkey Embedded Security Protects Designs from the Ground Up
Related Reference
About the Author
Paul Pickering
Paul Pickering has over 35 years of engineering and marketing experience, including stints in automotive electronics, precision analog, power semiconductors, flight simulation and robotics. Originally from the North-East of England, he has lived and worked in Europe, the US, and Japan. He has a B.Sc. (Hons) in Physics & Electronics from Royal Holloway College, University of London, and has done graduate work at Tulsa University. In his spare time, he plays and teaches the guitar in the Phoenix, Ariz. area