Cloud computing, as one reference put it, is just another term for accessing services via the Internet. For small companies that may be true, but larger companies and government agencies are establishing their own private cloud capabilities, so the comment should include these specific intranets as well. Whether public or private, the reasons for adopting cloud computing center around improvements to efficiency and cost.
At the very large end of the scale, the U.S. Department of Defense (DoD) is establishing an overall cloud structure that will consolidate its many separate computing facilities into a smaller number of networked core centers. A set of common applications will further streamline operations by reducing duplication.
In adopting the cloud paradigm, a bit of paranoia might be expected in organizations that traditionally have acquired, stored, and protected their own data, but how real is the perceived threat? Apparently, it’s very real, judging from a recent FBI briefing to businessmen. “‘You’re going to be hacked,’ Joseph Demarest, assistant director of the FBI’s cyberdivision, told the business leaders. ‘Have a plan,’ he advised.”1
A report on the 2014 CSA Congress and IAPP Privacy Academy events had a similar message, stating, “Cloud data breaches are inevitable… better data identification and classification [are needed] so that enterprises can concentrate their efforts on securing the data that matters most.” According to the report, 10% to 20% of the total data typically may be critical.2
How should an organization make this determination for a large amount of test data that cannot be duplicated—perhaps data that was acquired as a space probe crashed into an asteroid? National Instruments’ Automated Test Outlook 2014 report suggests, “Organizations that are concerned about software IP and data security along with system uptime can deploy a private cloud.” This is exactly what the DoD has done.
In the department’s July 2012 Cloud Computing Strategy document, the statement is made, “The DoD Enterprise Cloud Environment will include separate implementations and data exchanges on non-secure Internet protocol router network (NIPRNet), secure internet protocol router network (SIPRNet), and top secret sensitive compartmentalized information (TS SCI) security domains.” One assumes that within the TS SCI, for example, 100% of the data is critical.
The Defense Information Systems Agency (DISA) manages the DoD’s cloud program and provides the infrastructure-as-a-service milCloud as part of the program. As recently reported, Maj. Gen. Alan Lynn, DISA vice director, said, “If industry can come to us with a cloud solution that is cheaper [than milCloud], then we are going to do it. That’s the bottom line. And there are some things that we’re never going to put into a commercial cloud that we’ll need the milCloud for. So, we’re going to be able to live side by side with industry in the cloud in the future.”3
Reference 3 further quotes Lynn as saying, “…budgets are drying up,” and as a consequence, DISA is running a small pilot project to determine just how viable and less expensive commercial cloud services may be—in effect, how wide the milCloud-to-commercial cloud link can be made.
To that end, “DISA recently gave Amazon Web Services provisional authorization to operate at security impact levels 3 to 5 of the DoD Cloud Security Model, which would allow Defense Department components to use those cloud solutions for sensitive information falling under those levels.”3
Availability
High-value data that you cannot afford to lose is best protected by storing duplicate copies in physically separate locations. Many companies store periodic computer backups at multiple sites to ensure that should something catastrophic occur, the computer system state can be restored with minimal disruption.
Interestingly, the Amazon Web Services (AWS) organization takes the same approach. As explained in a Forrester Research white paper, “AWS data centers located in North America, Europe, Latin America, and Asia compose tier one of the AWS infrastructure. Each geographic region has from one to five availability zones (AZs). AWS AZs make up the second tier of the AWS infrastructure. Each AZ is made up of one or more data centers. These are physically located in separate buildings on separate power grids, in separate environmental disaster zones, with distinct network access points and separate electrical generator support.”4
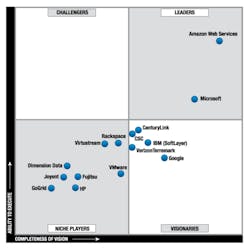
As shown in the figure, many companies offer cloud-based infrastructure services, although by Gartner’s definitions and analysis, AWS is the leader.5 Geographical considerations similar to those AWS used as well as DoD-specific issues resulted in the selection of Montgomery, AL; Mechanicsburg, PA; Columbus, OH; St. Louis, MO; Warner Robins, GA; Oklahoma City, OK; San Antonio, TX; and Ogden, UT, as locations for the eight Defense Enterprise Computing Centers that DISA manages. Clearly, the level of consolidation is high given that previously the DoD operated at least 200 separate centers.6
Courtesy of Gartner
The Army also is undergoing data center reduction, “…to eliminate 185 of its data centers by the end of 2015, according to Col. Chris Miller, chief of Army Data Center Consolidation at the Army CIO.” As part of the process, MicroTech is creating ruggedized, man-transportable portable cloud centers that can quickly be dropped into combat zones. Similar versions of the company’s MicroKloud product line are being used by the FBI and FEMA to provide highly versatile computing power in disaster recovery zones and domestic emergency scenes. Ideally, Army personnel would have cloud access anywhere in the world.
The primary resources that the Army accesses will be provided by the DoD’s own data centers. “Specialized needs will be handled by private sector contractors, or as a last resort, Army-owned data centers,” the article quoted Col. Miller as saying.7
In an article written about 18 months after reference 7, operational practicalities have dampened some of the earlier cost-saving exuberance. “… data center consolidation is on track… [with] a self-imposed target of 60% reduction by the close of fiscal 2018…said Neal Shelley, the Army Data Center Consolidation Plan lead.” As Shelley explained, additional attention was being placed on operational needs.
“‘In our business, light-speed matters,’ Shelley said. ‘There are things you cannot do remotely. The response time is not sufficient or it is so critical that you cannot have that application running several miles distant. So there will continue to be data processing going on at posts, camps, and stations.’”8
And, according to Gunnar Hellekson, chief technology strategist of the public sector division at open-source developer Red Hat, “‘When you have a war fighter who needs a mapping data service, for example, being able to deliver that over a cloud service becomes a completely different situation’ versus having a local server…. ‘You have to have a large amount of bandwidth, you have to have redundancy, while on the operational end you may have someone with just an intermittent satellite connection.’”8
Security
Will the new Army and DoD computing infrastructures be more or less secure than the previous ones? The answer involves many pros and cons but centers on the increased importance of “…data encryption, security checks, granting access to data based on different security levels, intrusion-prevention systems, and event correlation,” according to Alexandru Caitlin Cosoi, chief security officer at BitDefender.7
Encryption will be discussed in a companion article in the January 2015 issue.
References
- Kelly, E., “500M records stolen in 12 months,” USA TODAY, Oct. 21, 2014.
- Wright, R., “Experts: Expect cloud breaches to endanger data privacy,” SearchCloudSecurity.com, Sept. 23, 2014.
- Cheng, J., “Amid shrinking budgets, DISA turns to the commercial cloud,” DefenseSystems, Sept. 5, 2014.
- Ferrara, E., AWS Cloud Security, Forrester Research, Feb. 5, 2014.
- Leong, L., et al, Magic Quadrant for Cloud Infrastructure as a Service, Gartner, Report ID G00261698, May, 2014.
- Gore, L., Montgomery selected as one of eight sites for Department of Defense Core Data Center, Alabama Media Group, July 19, 2013.
- Dysart, J., “Army private cloud to attack IT sprawl and save millions,” Defense Systems, March 22, 2012.
- Stone, A., “DISA to take responsibility for DoD’s core data centers,” Defense News, Oct. 1, 2013.
For more information
Amazon Web Services
BitDefender
Forrester Research
Gartner
MicroTech
National Instruments
Red Hat