Serving and Securing Next-Generation Cloud Applications with a Multikernel RTOS
Society continues to embrace technology, and advanced application spaces are being created/renewed/addressed in new and interesting ways. Our future Cloud-enabled IoT-oriented Smart Cities/Factories/Homes will be gleaming multipurpose wonders of engineering, providing everyone with everything they need.
Maybe. All those shiny happy people with shiny happy devices need shiny happy functionality and infrastructure to operate. That wireless future has a lot of wiring behind the wainscotting, and that’s just on the hardware side. The software side of the coin is even more complex and interwoven, as anything operating in the world today must be multilingual, multimodal, and multiprotocol in order to provide the desired level of functionality. It takes quite an advanced architecture to keep things simple for end users.
Fast, powerful computing
One of the companies addressing the need for powerful and flexible computing is eSOL, currently the provider of eMCOS, a true multikernel RTOS. The company is looking towards emerging automotive and industrial use-cases requiring high-throughput multicore computing. Offering flexibility and scalability, eMCOS is also optimized for software-defined architectures for future edge computing and other advanced embedded application spaces such as autonomous vehicles and real-time Industrial IoT, as well as applications like automation or robotics.
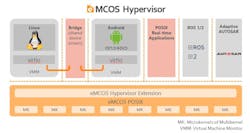
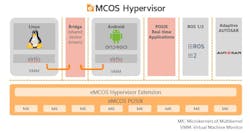
eSOL recently showcased their eMCOS Hypervisor at this year’s embedded world Exhibition & Conference DIGITAL, showing how it can address the needs of design and development engineers in the embedded industry. eMCOS Hypervisor enables the integration of both RTOS and general-purpose OS to run concurrently on a single hardware platform, with full time and space isolation provided inside a mixed-criticality system. It also enables the implementation of the open-standard virtio interface for sharing physical or virtual resources, to allow re-usage of Linux applications code, among other useful things.
We reached out to Rolland Dudemaine, Vice President of Engineering at eSOL Europe, about the eMCOS Hypervisor and how it aids the engineer. Our discourse opened with him underscoring that one of the most important aspects of software development is reusability, and eSOL’s eMCOS Hypervisor implements support for common virtio device interfaces. This allows a Guest OS to access shared devices, making it possible to deploy a Linux image without other modifications than the integrator-level device-tree to specify both physical and virtual devices.
Rolland also pointed out that the eMCOS Hypervisor supports sharing physical devices using ‘bridges’ running as POSIX real-time applications directly on the Hypervisor native environment, without the overhead of a Controlling Guest OS. These bridges can act as simple software-defined routers, as well as implement specific functionalities like encryption, an intrusion-detection-system, and/or rate limiting. Physical devices can even be directly passed to the Guest OS, for best reuse of existing device drivers without sharing capability.
Scalability and security
eMCOS is a highly scalable RTOS using a distributed microkernel approach to their architecture that enables scalability, supporting increasing core counts and heterogeneous hardware configurations, including different architectures such as on-chip flash microcontrollers, GPUs, and FPGAs. The platform is not only already ported to several hardware architectures, but can also be easily ported to other platforms with its highly portable source code and design.
eSOL also has a novel scheduling algorithm that provides real-time capabilities offering the performance and scalability expected from multicore processors, and uses the same programming model and POSIX interface as other widely used RTOSes for single- and multi-core processors.
When questioned about security, Rolland brought up the collaborative effort eSOL has with Karamba Security, combining eSOL’s eMCOS and Karamba’s XGuard solutions to offer advanced cyber-protection for connected cars and smart-factory equipment. Rolland explained by extending XGuard support to protect eMCOS and eMCOS Hypervisor, customers will benefit from an advanced OS architecture with seamless protection of customer applications.
Integrating the cyber-protection features of eMCOS and Karamba’s XGuard platform delivers unprecedented assurance for mission-critical and safety-critical connected assets. In addition to strengthening attack resistance, the resulting solution secures applications proactively through advanced monitoring and analysis. When running on eMCOS, Karamba’s XGuard enables applications to protect themselves against cyber-attacks, with automatic policy generation to identify legitimate binaries, as well as anti-tampering and event reporting of attacks to assist root-cause analysis.
The XGuard embedded security agent also connects to Karamba’s XGuard Monitor to provide continuous attack detection and response. Leveraging hybrid local and cloud-level analytics, XGuard product suite features powerful forensic tools to identify attackers’ behavior and generate actionable intelligence.
When asked about how eMCOS addresses the current and future needs of open-source applications developers, Rolland said that eMCOS POSIX, as a scalable platform, is proposing a familiar POSIX-compliant, multi-process environment, to allow running diverse frameworks, both commercial and open-source. This can span from basic Unix-style shell tools, to more advanced ROS and Autoware, to many web and embedded libraries. Many of our customers already use their own open-source frameworks as well.
eMCOS Hypervisor, as an extension of eMCOS POSIX, goes to the next level, and allows running entire Linux or other OS as Guest environments. By following open standards like virtio, we allow fast reusability of existing drivers without the need to create custom branches of Linux.
This allows customers to control in a fine-grained manner how they want to reuse or extend open-source software, whether it will be in an underprivileged environment in a Guest, or directly on the real-time POSIX environment, or even both of course.
When it comes to cyber-security in embedded systems, security is always about analyzing the attack surface, and isolating the weakest link. While this weakest link is many times open-source software, the most critical security issues often circle around device drivers, which are either part of the attack surface or part of what the hacker wants to exploit. Therefore, running drivers in the context of user applications that can themselves be sufficiently isolated is advised on eMCOS POSIX, and brings general isolation capabilities to the entire platform, following a microkernel model.
This allows open-source, commercial, project-specific software and drivers to cooperate in a well-organized, efficient manner, while maintaining an acceptable level of security. And a great performance, since eMCOS features its multikernel approach for ideal parallelism and Freedom From Interference (FFI). Now, there is always a balance between the effort to reach an acceptable level of security, an acceptable level of Functional Safety, an acceptable performance, and an acceptable development time. Rolland emphasized they are always present to consider all these aspects with their customers, and help them focus on the differentiating aspects of their products.
Security is good policy
One important aspect is the enforcement of security policies, to ensure that applications themselves are running unmodified, are only doing what they should be authorized to do, and that only applications that were approved in the first place can even start. eMCOS POSIX and Hypervisor have the necessary frameworks in place to allow such verification, and rely on proven approaches in the field of cryptography and authentication to do the initial authorization and corruption detection.
Karamba Security is a good example of such a field-proven expert company they integrate with. For instance, CFI authentication can be applied to some or all applications in a system to do verification of every call of the application. In addition, application whitelisting can be added to the platform to cryptographically guarantee that the application starting is indeed allowed for this specific device. This helps build a chain of trust, from secure boot to secure execution.
In closing, Rolland finished by emphasizing the need to address security issues early on, and finding the weakest link is very important. When software and hardware architects, developers and integrators are conscious of what is required to create a safer and more secure system, many of the design and implementation considerations are taken differently, and often in a more optimal way. Creating a culture of security and safety makes everything cleaner in the long term, and less hackable as a result.
About the Author
Alix Paultre
Editor-at-Large, Electronic Design
An Army veteran, Alix Paultre was a signals intelligence soldier on the East/West German border in the early ‘80s, and eventually wound up helping launch and run a publication on consumer electronics for the US military stationed in Europe. Alix first began in this industry in 1998 at Electronic Products magazine, and since then has worked for a variety of publications in the embedded electronic engineering space. Alix currently lives in Wiesbaden, Germany.
Also check out his YouTube watch-collecting channel, Talking Timepieces.