Today’s vehicles are essentially supercomputers on wheels. Any new car has more computing power than NASA had for getting astronauts to and from the moon. The latest advanced driver-assistance systems (ADAS) and self-driving cars are increasing the computational performance requirements. Keeping this software updated is leading to the requirement for over-the-air (OTA) updates. Likewise, delivering cars with services like Android Auto, Apple’s CarPlay, and Amazon’s Alexa are requiring wireless communication with the internet.
Now step back and consider PC and software attacks that have become so common, subsequently spawning a host of companies that are trying to lock down Microsoft Windows from attack. Windows isn’t the only mark out there, but it tends to have the largest number of targets for attackers. It has also been a softer target because of its availability and complexity. Likewise, the operating system isn’t always the only target to compromise a Windows computer. More likely, the applications or services like Adobe’s Flash or Oracle’s Java have been focuses as well. Many of these services and related attacks are brought on by users.
A system doesn’t have to be completely compromised to be exploited. A wide range of attacks, from ransomware to stealing cycles to generating bitcoins, can make a PC do something that the user would not like.
These New Cars Are So PC
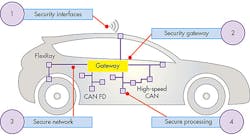
The problem with new cars is they’re becoming more like PCs in that users can add services or apps to the mix. Automotive electronics are actually much more complex than that of the PC or smartphone managed by users. In fact, the typical car has multiple networks and platforms connected to these (see figure). Manufacturers have made security a priority with varying levels of success, but those networks and nodes are likely more secure than any home and most commercial environments.
Automotive security needs to address a wide range of services within the car.
That said, cars are becoming more user-configurable and open to the types of apps and services found on PCs that are prone to attacks. Likewise, the platforms that these run on are becoming more standardized. There’s no comparable automotive Windows solution, but platforms like Android are coming close.
Car companies are designing their systems to try to isolate systems, and it may be that an attacker may not be able to control the accelerator or brakes. However, if an attacker can control the sound and volume or the windows, then problems related to driver distraction may arise that could indirectly cause fatalities.
It’s impossible to prevent all attacks given the drive for more connectivity and customization in the car. The questions, then, are who will be responsible for what aspects of security, how open or flexible will a system be, and will OEMs or platform providers support providers of third-party services, apps, and hardware (and what security rules or requirements exist)?
The problem is large and complex, but not limited to cars. Arm’s Platform Security Architecture (PSA) looks to address the security space in general. It’s definitely applicable, given the widespread use of Arm technology within the car.
Securing the vehicle will be a cooperative effort, starting with the manufacturers. The challenge continues to be how open a platform should be versus how much security should be in place. Moreover, how well will the pieces work within that framework? Getting the consumer to understand what’s going on under the hood will probably be a lost cause, but they need to be protected even if they give an app access to everything under the sun.
About the Author
William G. Wong
Senior Content Director - Electronic Design and Microwaves & RF
I am Editor of Electronic Design focusing on embedded, software, and systems. As Senior Content Director, I also manage Microwaves & RF and I work with a great team of editors to provide engineers, programmers, developers and technical managers with interesting and useful articles and videos on a regular basis. Check out our free newsletters to see the latest content.
You can send press releases for new products for possible coverage on the website. I am also interested in receiving contributed articles for publishing on our website. Use our template and send to me along with a signed release form.
Check out my blog, AltEmbedded on Electronic Design, as well as his latest articles on this site that are listed below.
You can visit my social media via these links:
- AltEmbedded on Electronic Design
- Bill Wong on Facebook
- @AltEmbedded on Twitter
- Bill Wong on LinkedIn
I earned a Bachelor of Electrical Engineering at the Georgia Institute of Technology and a Masters in Computer Science from Rutgers University. I still do a bit of programming using everything from C and C++ to Rust and Ada/SPARK. I do a bit of PHP programming for Drupal websites. I have posted a few Drupal modules.
I still get a hand on software and electronic hardware. Some of this can be found on our Kit Close-Up video series. You can also see me on many of our TechXchange Talk videos. I am interested in a range of projects from robotics to artificial intelligence.