What’s the Difference Between Blockchains, Cryptocurrency, Audit Trails, and Databases?
Blockchains are nothing more signed, peer-to-peer, distributed ledger databases. Okay, we’re all done here.
No?
Alright, blockchains are a bit more complicated than that–and more useful than they might sound. Most will know blockchains from BitCoin, one of the many cryptocurrencies based on them. But cryptocurrencies are only one use for blockchains. Before getting into applications, let’s take a look at what a blockchain system looks like and how it operates.
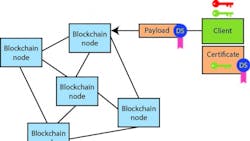
To start, you need to know about public key encryption and digital signatures, because the blocks in a blockchain are digitally signed and the blockchain nodes are authenticated to each other (Fig. 1). This allows them to maintain their copy of the blockchain and determine whether information from other nodes is accurate. Those providing nodes to the blockchain must also have their own encryption keys so they can sign their blocks.
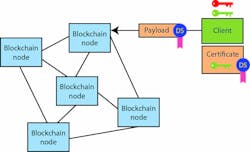
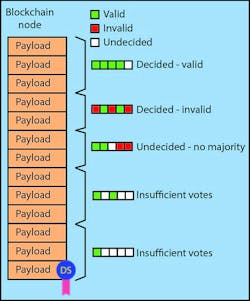
A blockchain is actually a logical entity maintained by a blockchain node. It is designed to be a mostly read-only database that grows over time as blocks are added (Fig. 2). Block payloads are accepted by a node and distributed to its peers. There is an acceptance process and verification of digital signatures, but eventually a block will be validated by enough nodes for the block to be permanently added to the blockchain.
At this point, the added block will be replicated in a majority of nodes, and the rest will eventually catch up. This means that all nodes will have a moving high water mark that the collection of nodes agrees with, but the databases will probably not be identical across all the nodes at any point in time.
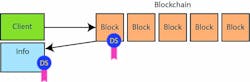
The idea is that the payload of a block can be accessed by an external entity and used to generate a subsequent block that will get incorporated into the blockchain. A typical example is where a block contains a logical value that is split in half and assigned to two new blocks. The signatures for these new blocks can be used to allow one of the new blocks to contain this new value. Incorporating the new blocks into the blockchain will mark the original block as used and the two new blocks as active.
The system is robust because the blockchain database is replicated. All nodes can accept new blocks and all nodes do not have to be active or accessible all the time although a quorum is needed to activate new blocks.
The challenge for blockchain systems is to maintain performance and scalability as the system grows. A lot depends upon the frequency of updates and the number of systems involved overall in addition to the network. Many blockchain systems operate on the internet, but that isn’t a requirement. They can be used in closed networks as well.
Cryptocurrency
So, back to cryptocurrencies.
A cryptocurrency is a digital asset that can be an exchange medium. These days, cyptocurrencies tend to be implemented using a blockchain. This allows transactions using the cryptocurrency to occur in a decentralized, distributed fashion. Cryptocurrencies are relatively new (the aforementioned Bitcoin started in 2009).
The payload of a block indicates the amount of money involved in a transaction. How these values are created and manipulated depend upon the system being employed and the players involved in the system. Most cryptocurrencies use a timestamping scheme so a trusted third party does not need to be involved in the system.
Most cryptocurrency systems use a proof-of-work scheme to create a new block or BitCoin. BitCoin uses proof-of-work schemes are based on SHA-256. It is also used by LiteCoin. It is also possible to use proof-of-stake schemes as well.
BitCoins are created by “mining.” This uses the hashcash proof-of-work function that is designed to take a lot of computational cycles but not much else. Specialized hardware has been developed to create BitCoins. The amount of time needed to generate just one BitCoin varies significantly depending upon the hardware used.
Other Blockchain Applications
Just about any application that requires a registered ledger is a candidate for blockchain support. Many embedded applications simply need a single database, but if there is a need for a more robust solution, blockchains might make sense.
Blockchains have been touted as solutions for all sorts of applications. For example, there are a number of efforts to use them in educational environments. In this instance, the various records, testing, and certifications a person earns are tracked using blocks. This approach allows for the distribution of this information. The blocks normally do not contain all the information, but rather, links to digitally signed packages.
Blockchains can also be used for conventional ledger-based applications. These applications include backend clearing and settlement. They could be used in real estate transactions, for tracking music or other multimedia content, or even for handling contracts.
Blockchain use is still in its infancy. Security remains a key component and it should not be overlooked when considering or using this technology. Incorrect implementations can cause significant security problems. Developers also need to consider the scope of implementation, frequency of updates, and hardware and storage requirements.
About the Author
William G. Wong
Senior Content Director - Electronic Design and Microwaves & RF
I am Editor of Electronic Design focusing on embedded, software, and systems. As Senior Content Director, I also manage Microwaves & RF and I work with a great team of editors to provide engineers, programmers, developers and technical managers with interesting and useful articles and videos on a regular basis. Check out our free newsletters to see the latest content.
You can send press releases for new products for possible coverage on the website. I am also interested in receiving contributed articles for publishing on our website. Use our template and send to me along with a signed release form.
Check out my blog, AltEmbedded on Electronic Design, as well as his latest articles on this site that are listed below.
You can visit my social media via these links:
- AltEmbedded on Electronic Design
- Bill Wong on Facebook
- @AltEmbedded on Twitter
- Bill Wong on LinkedIn
I earned a Bachelor of Electrical Engineering at the Georgia Institute of Technology and a Masters in Computer Science from Rutgers University. I still do a bit of programming using everything from C and C++ to Rust and Ada/SPARK. I do a bit of PHP programming for Drupal websites. I have posted a few Drupal modules.
I still get a hand on software and electronic hardware. Some of this can be found on our Kit Close-Up video series. You can also see me on many of our TechXchange Talk videos. I am interested in a range of projects from robotics to artificial intelligence.