Low-Cost Security Solutions Simplify IoT Cloud Connectivity
Download this article in PDF format.
The Internet of Things (IoT) adds wired or wireless connectivity to a slew of applications: factory automation, automobiles, medical equipment, smart cities, smart farms, building and home automation, appliances, smart grids, personal electronics, and many more.
In many cases IoT edge nodes are designed with embedded processors with only enough functionality to provide the required performance at low cost, so they don’t have enough spare processing power to implement a full array of security measures, or even any at all.
The billions of nodes present rich opportunities for mischief. Hackers can take control of multiple devices to build a botnet. Then they can use the combined computing power to send spam, spy on organizations, mount distributed denial of service (DDoS) attacks, or even amass Bitcoins through cryptomining (Fig. 1).
1. Coming soon to an IoT device near you. (Source: HDQwalls.com)
Sponsored Resources:
- Secure IoT Sensor Node
- ATECC608A CryptoAuthentication™ Device
- Use a Crypto Chip to Add Secure Boot to IoT Device Designs
Several well-publicized events—hacked cardiac devices, baby monitors, security cameras, and, of course, the Mirai botnet—have underscored the need for designers to improve security from the edge node to the cloud.
Providing security for an embedded design has multiple layers. Designers must conduct a thorough risk evaluation and select appropriate measures so that an embedded node includes the needed level of security while still providing the proper functionality and keeping within the cost targets. Not an easy job!
Manufacturers have well-established internal procedures to protect data before the product leaves the factory: permission-based access controls, levels of user privilege, strong passwords, encryption when data is being moved and while it’s being stored, activity logging, and so on.
There’s also an additional set of external security issues that involve the interaction between the device and the cloud. The manufacturer must have a means of transmitting data securely into the cloud. Once the product is deployed in the field, there must be a way to ensure that only authorized devices have access to cloud resources and that devices only accept verified data from a trusted source.
Major cloud providers are acutely aware of the potential security issues inherent in IoT applications. Amazon Web Services (AWS) IoT Core, Google Cloud IoT Core, and other providers offer comprehensive sets of tools to help in this process.
Microchip’s CryptoAuthentication for IoT Applications
Strong authentication is the foundation of robust IoT security. Cloud providers are driving toward hardware-based security for strong device identity protection and to prevent identity spoofing, as well as protect against unauthorized firmware updates.
Microchip offers the industry's widest selection of authentication devices featuring hardware-based root-of-trust storage and cryptographic countermeasures. The company's ATECC608A CryptoAuthentication secure element provides a secure authentication solution for Google IoT Core and AWS IoT. The part implements a complete asymmetric-key cryptographic solution based on the elliptic-curve Diffie-Hellman (ECDH) security protocol and the elliptic-curve digital signature algorithm (ECDSA). ECDH is an ultra-secure method to provide key agreement for encryption/decryption; ECDSA offers sign-verify authentication for IoT devices.
With integrated ECDH and ECDSA, the ATECC608A supplies the full range of IoT security tools—confidentiality, and data integrity—to systems with microcontrollers (MCUs) or microprocessors (MPUs) running encryption/decryption algorithms. The ATECC608A’s hardware executes the cryptographic solution up to 1000X faster than software running on a standard microcontroller. In addition, the part includes an integrated AES hardware accelerator to provide hardware-based security for LoRaWAN applications, plus enable small microcontrollers to have secure boot capabilities.
The ATECC608A is compatible with Microchip’s AVR/Arm MCU or MPU, as well as other MCUs or MPUs. In common with other CryptoAuthentication devices, the ATECCC608A delivers extremely low power consumption, communicates via I2C or a single-wire interface (SWI), and has a tiny form factor, making it ideal for space-constrained or battery-powered IoT applications.
Each ATECC608A ships with a guaranteed unique 72-bit serial number. This allows a host system or remote server to verify a signature of the serial number to prove that the serial number is authentic and not a copy.
Connecting the ATECC608A to the Google Cloud: Overview
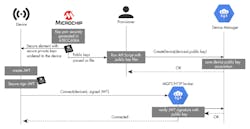
2. Microchip and Google have developed a simple authentication protocol for IoT devices that employ the ATECC608A’s unique features. (Source: Google)
A sample IoT authentication sequence (Fig. 2) using the ATECC608A and Google Cloud IoT Core is as follows:
1. Start with a secure element. Any secure element stores private keys and blocks all attempts to physically hack the device and retrieve the keys. The ATECC608A, though, not only stores the private keys, but also validates the firmware and provide a more secure-boot capability for the device.
The ATECC608A generates its own private key internally instead of using a key from an external Certificate Authority (CA). The chip uses a true random-number generator (TRNG) to create the key, making it virtually impossible to derive, and the key remains internal to the device. Using the private key, the chip can generate a public key that can be signed by the chosen CA of the ATECC698A customer.
Microchip performs this signature in a dedicated and secure U.S. facility where the customer’s intermediate CA keys are stored in a secure server connected to the manufacturing line. The key pairs and certificates are all generated in a controlled environment, enabling auditing and a high level of encryption.
Once the secure elements have each generated their key pairs, the corresponding public keys are sent to the customer’s Google Cloud account and stored securely in the Cloud IoT Core device manager. Because Cloud IoT Core can store up to three public keys per device; key rotation can be performed without any issues.
2. Use a JWT for authentication. TLS can establish secure communication between the device and the cloud. TLS can also provide authentication, but the TLS authentication stack is large; Google Cloud IoT Core employs a JWT (JSON Web Token) to authenticate the device because it’s more suitable for a resource-limited IoT device. A JWT is an open standard (RFC 7519) that defines a compact and self-contained way to transmit information securely between parties as a JSON object. The information in a JWT can be verified and trusted because it’s digitally signed. JSON is a standard text-based format for representing structured data as a series of key/value pairs.
Using this approach, the IoT device will establish a secure connection to the Google Cloud endpoint with TLS; it then generates a JWT, signs it with its private key, and passes it as a password. The Google Cloud endpoint receives the JWT and verifies the signature using the device's public key, thus establishing mutual authentication. The cloud customer can limit the duration of the JWT validity.
There are several benefits to combining the JWT method with the ATECC608A. The approach doesn’t depend on the TLS stack for device authentication, so updating to the recently finalized TLS 1.3 will be straightforward. IoT devices don’t need to store their public key and certificate or host a full TLS stack. Both reduce the memory requirement to well under 50 kB, possibly allowing the designer to move to a lower-cost MCU.
IoT Sensor Node Simplifies Evaluation of IoT Device Connectivity
To demonstrate the ease-of-use of the ATECC608A in a Google Cloud IoT Core environment, Microchip incorporated the part into a sensor node board (Fig. 3). The AVR-IoT WG (part # AC164160) is a compact and inexpensive evaluation and development board that demonstrates the easy migration of bare-metal embedded-control applications to the Google Cloud. The kit includes hardware, software, and access to a sandbox account, so a designer can get online and begin evaluation in only a few minutes.
3. With the included hardware and software, the AVR-IoT WG allows a designer to begin evaluation in a few minutes. (Source: Microchip Technology)
In addition to the ATECC608A, the core components are:
- The AVR ATmega4808 microcontroller features the 8-bit AVR processor running at up to 20 MHz with a hardware multiplier, 6-kB SRAM, 256 bytes of EEPROM, and up to 48 kB flash in a 32-pin package. The part uses the latest Core Independent Peripherals with low-power features, including Event System, intelligent analog, and advanced peripherals.
- The WINC1510 network controller is a single-band, 2.4-GHz b/g/n network controller optimized for low-power IoT applications. The part supports a variety of security protocols: WPA/WPA2 Personal and Enterprise, TLS, and SSL. The IoT sensor board also integrates the Wi-Fi antenna.
- The nEDBG “Nano Embedded Debugger” allows connection to development kits for ATmega4808 and other Microchip MCUs, as well as supports programming and debugging support via the company’s MPLAB X and Studio 7.0 IDE. The nEDBG offers a serial connection to a USB interface to provide data-streaming capabilities between the host computer and the onboard MCU, plus a mass storage interface for easy “drag and drop” programming.
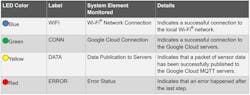
The AC16460 also includes a TEMT6000 ambient light sensor and a Microchip MCP9808 temperature sensor, plus two user-configurable buttons and indicator LEDs that signify status (Fig. 4).
4. LEDs on the AVR-IoT WG provide convenient status indications. (Source: Microchip Technology)
The AVR-IoT WG comes preprogrammed and configured for demonstrating connectivity to the Google Cloud IoT Core. The ATECC608A on the board is pre-registered at Microchip’s AVR-IoT (sandbox) account on Google Cloud. Each secure element provides an 18-digit hexadecimal Unique Identification Number (UID) and a public or private key pair, pre-generated using elliptic-curve cryptography.
The UID can be viewed on the URL of the webpage application or via the serial command line interface. The ATECC608A private key is never revealed, but the public key can be viewed in the included PUBKEY.TXT file or via the serial command line interface.
Since the ATECC608 is pre-registered, the application only needs a Wi-Fi network with an internet connection to stream data to the Google Cloud.
CryptoAuthLib Software Library Speeds JWT Authentication
Microchip’s Crypto Authentication Library (CryptoAuthLib) is a software library designed to work with CryptoAuthentication devices like the ATECC608A. CryptoAuthLib incorporates management features for Public Key Infrastructure (PKI) X.509 certificates, saving the developer much time writing certificate management code for a specific driver. It also helps when integrating TLS into ECDH-capable CryptoAuthentication devices.
CryptoAuthLib eases the implementation of secure IoT features such as the Google JWT authentication protocol discussed above. Complex security operations are accessed through a set of function calls provided by the CryptoAuthLib application programming interface (API).
The library is divided into several API categories that cover a variety of crypto-authentication application needs. These APIs include:
- Basic API—emphasizes ease-of-use
- Core API—allows use of any device feature
- PKI X.509 Certificates—PKI applications that store and retrieve X.509 certificates
- PKI TLS—secure communication key agreement protocols
- Crypto Utilities—general software hash implementations
- HAL—hardware abstraction layer integrates with physical interfaces
CryptoAuthLib is written in C, making it suitable for multiple platforms such as Arm Cortex devices and Windows and Linux machines.
The Microchip Security Portfolio
Microchip offers a range of products for other security applications. Security-focused MCUs include the 16-bit PIC24FJ256GB412 devices with an integrated hardware Encryption Engine, and 32-bit SAM L11 and SAM D5x/E5x MCUs. Among the security-focused MPUs are the SAMA5D2 and SAMA5D4. Furthermore, several product families help designers add security into embedded systems:
- The Trusted Platform Module (TPM)family provides strong hardware-based public key (RSA) security on a single device for personal and tablet computers and embedded processor-based systems.
- CryptoMemory products are cost-efficient, high-security, electrically erasable programmable read-only memory chips (EEPROMs) and host-side security for applications requiring comprehensive data protection.
- CryptoRF is a 13.56-MHz RFID device family that includes a 64-bit embedded hardware encryption engine, mutual authentication, and up to 64 kb of user memory.
Microchip’s broader security ecosystem includes Security Design Partners with TLS stack providers, Cloud experts, Certificate Authority companies, and CryptoAuthLib library experts.
Conclusion
As a part of their comprehensive portfolio of security products, Microchip Technology has developed the ATEC608A secure element to simplify the task of connecting an IoT device to the cloud. Microchip has combined with Google to offer a convenient hardware-based root of trust for Google Cloud IoT Core.
Sponsored Resources:
- Secure IoT Sensor Node
- ATECC608A CryptoAuthentication™ Device
- Use a Crypto Chip to Add Secure Boot to IoT Device Designs
Related Resources
- TheCircuit blog: “Microchip’s Secure IoT Sensor Node”
- “Getting Started With Your AVR-IoT WG Development Board” video
About the Author
Paul Pickering
Paul Pickering has over 35 years of engineering and marketing experience, including stints in automotive electronics, precision analog, power semiconductors, flight simulation and robotics. Originally from the North-East of England, he has lived and worked in Europe, the US, and Japan. He has a B.Sc. (Hons) in Physics & Electronics from Royal Holloway College, University of London, and has done graduate work at Tulsa University. In his spare time, he plays and teaches the guitar in the Phoenix, Ariz. area