There’s bad news in the paper, The Unpatchable Silicon: A Full Break of the Bitstream Encryption of Xilinx 7-Series FPGAs by Maik Ender and Amir Moradi, Horst Goertz Institute for IT Security, Ruhr University Bochum, Germany; and Christof Paar, Max Planck Institute for Cyber Security and Privacy and Horst Goertz Institute for IT Security, Ruhr University Bochum, Germany. The hack has become known as Starbleed and the general press has hyped the doom and gloom because FPGAs are these “magical devices found everywhere and there’s no fix.”
The paper is actually quite good and the attacks it presents are valid. Xilinx has confirmed that a software fix isn’t possible, but a few details need to be considered before panicking.
Two attacks that target the Virtex-6 and -7 Series FPGAs are outlined in the paper. “The first attack breaks the confidentiality of any encrypted design using the FPGA as a decryption oracle. The second attack breaks the authenticity by using the same oracle to encrypt arbitrary bitstreams and generating a valid authentication tag.”
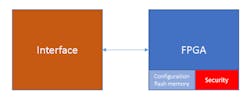
In both cases, the issue is associated with systems that need the encryption support. Both FPGA platforms implement a RAM-based FPGA that uses an external device for the configuration information loaded at boot time (Fig. 1). Protection of the FPGA IP is sometimes—but not always—critical. Likewise, gaining access to the storage device remotely may not be possible. It’s possible with physical access to a device, but then so are other methods to attack a device.
The ability to reprogram the serial storage may also be prevented using other means depending on how it can be updated. It’s often up to an external system or microcontroller where additional protections may exist or could be added. A field-upgradable system would have this type of feature, so mitigation of an attack on the FPGA could be handled there.
Access…Denied?
The attacks outlined in the paper need access to “the encrypted bitstream and either the JTAG or the SelectMap configuration interface.” Though physical access to a device provides this capability, remote access can be a challenge. Devices without network connectivity aren’t at risk of remote attacks.
Even gaining access to FPGA IP doesn’t guarantee an easy attack vector. Unlike a processor, an FPGA depends on its physical context. The interfaces are unique to each application. The configuration of an FPGA is arbitrary and capricious, but it can only affect what’s provided by the interface.
Likewise, if the interface isn’t manipulated properly, then the device can’t be compromised properly. This is more of an issue for standard platforms like the FPGA boards being used in data centers. However, they’re using newer FPGAs from Xilinx that are immune from these particular problems.
Flash-based FPGAs, or flash FPGAs, are one alternative to RAM-based FPGAs. These flash-based systems keep their software configuration on-chip (Fig. 2). Other potential attacks for these devices exist, but the success of these attacks depends on the quality of the protection, which tends to be substantial especially given the inability to gain direct access to the flash memory.
High-security flash FPGAs typically incorporate a physical unclonable function (PUF) as part of the physical and electrical architecture. These designs also significantly reduce the attack surface for the system.
Xilinx Virtex-6 and 7-Series FPGAs are found everywhere from aircraft to toys. I don’t want to downplay the severity of the problems Ruhr University researchers revealed. However, compared to many of the other attacks a system may be vulnerable to, this is a relatively minor one. Attacks on hard-disk-drive firmware are just as frightening because it allows an attacker to replace a system with an undetectable counterpart, and creating or modifying conventional software is much easier than changing FPGA IP.About the Author
William G. Wong
Senior Content Director - Electronic Design and Microwaves & RF
I am Editor of Electronic Design focusing on embedded, software, and systems. As Senior Content Director, I also manage Microwaves & RF and I work with a great team of editors to provide engineers, programmers, developers and technical managers with interesting and useful articles and videos on a regular basis. Check out our free newsletters to see the latest content.
You can send press releases for new products for possible coverage on the website. I am also interested in receiving contributed articles for publishing on our website. Use our template and send to me along with a signed release form.
Check out my blog, AltEmbedded on Electronic Design, as well as his latest articles on this site that are listed below.
You can visit my social media via these links:
- AltEmbedded on Electronic Design
- Bill Wong on Facebook
- @AltEmbedded on Twitter
- Bill Wong on LinkedIn
I earned a Bachelor of Electrical Engineering at the Georgia Institute of Technology and a Masters in Computer Science from Rutgers University. I still do a bit of programming using everything from C and C++ to Rust and Ada/SPARK. I do a bit of PHP programming for Drupal websites. I have posted a few Drupal modules.
I still get a hand on software and electronic hardware. Some of this can be found on our Kit Close-Up video series. You can also see me on many of our TechXchange Talk videos. I am interested in a range of projects from robotics to artificial intelligence.