Prevent Automotive Counterfeiting with Secure Authentication
This article is part of the TechXchange: Chip Shortages and Counterfeits
As the electronic systems in today’s cars become more sophisticated, it rapidly ramps up the number of sensors feeding mission-critical data into the electronic control unit (ECU). For drivers, it’s imperative to feel confident that the advanced driver-assistance system (ADAS) hasn’t been compromised by something as seemingly benign as an auto-repair shop using non-authentic parts to repair the vehicle. Likewise, an OEM would want to mitigate liability in these situations and notify consumers if the system, and thus driver safety, has been compromised.
How can you prevent counterfeiting in your automotive designs?
After discussing the threats faced by today’s electronically sophisticated automotive systems, this article explains how secure authentication can counter these risks.
Growing Problem of Non-Genuine Automotive Parts
The automotive industry is currently undergoing the biggest change in its history since Henry Ford developed the assembly line. With more companies moving toward electric vehicles, rapidly developing vehicle autonomy, and longer lists of in-cabin entertainment features coming to market, the breadth of automotive innovation is quite astounding. The increase in electronic components, however, means that there are more points of vulnerability inside vehicles than ever before.
As automotive OEMs progress toward fully autonomous vehicles, fears grow that self-driving cars will be easily hacked. Case-in-point: the well-publicized white-hat hackers’ effort to remotely kill a Jeep during a highway drive a few years ago.1 Indeed, the problem of fake parts has been a mounting area of concern in the automotive industry, as evidenced by the problems they can trigger. For example:
- Counterfeit airbags may not deploy properly after a collision.
- Fake engine and drivetrain components can cause engine failure or even fires.
- Non-genuine body parts may not perform as expected in a collision.
- Improperly made brake pads may compromise the vehicle’s stopping capabilities.
- Fake windscreens can shatter or displace.2
As ADAS continues to proliferate, every camera’s or sensor’s role in keeping the driver safe grows exponentially. It’s imperative that these components are genuine and not replaced by low-grade counterfeits that might not have the same range of field, proper resolution, or calibration that’s expected by the system.
Techniques to Secure Automotive Designs
It’s no surprise that when a lot of people think “security,” their minds automatically associate this with “software.” It’s undeniable that as cars continue to get smarter and rely more heavily on data from over-the-air (OTA) updates, secure software is a key component to protecting the automotive ecosystem, as well as ensuring that the data being sent to and from the car is private and its integrity is intact. OTA updates are outside the scope of this paper, but they aren’t outside the scope of the security discussion at a higher level.
However, when it comes to protecting peripheral systems in cars, hardware security remains key—pun intended. This brings us to the first point of why hardware security is a necessity: key management. Ordinary flash memory doesn’t guarantee protection from invasive probing attacks. This means that a hacker can modify the flash content or even inject other authority keys into the flash memory.
Why is this key such a big deal? This “key” is the device’s identity. If hackers can extract and clone this key, that means they can make as many clones as they want and that all of these clones would be read as a valid part of the system. Going a step further, having knowledge of the private key would allow a clone to sign data and send this data to the ECU and convince the system that this data is valid! Security, and thus clone prevention and the system’s integrity, relies entirely on the fact that the private key is unclonable and immutable.
What About HSMs?
So, if software security isn’t enough to stop attacks on automotive systems, what else can be done to prevent a breach of security? Many systems are moving toward the implementation of hardware security modules (HSMs) to secure various components within a system. Although HSMs are a great way to implement hardware security within a system, they can be costly and are often larger in size and greater in complexity than a standalone authenticator.
As a result, HSMs are often a great choice for adding security in the larger, more centralized systems within the car, such as one of the many ECUs. HSMs are especially necessary in cases where large quantities of data may need to be encrypted or validated, like when that data is being pushed up to the cloud for, say, OTA updates.
With more OEMs opting for OTA updates, the threat of malware infecting a vehicle’s ecosystem is more of a concern than ever before. It’s pertinent to driver safety that every update is validated and authenticated. In a similar vein, with sensitive vehicle information, such as driver location, being sent to the cloud, it’s important that any communication between the vehicle and the cloud is protected.
However, to secure smaller peripherals within a car, such as a camera or sensor, size and cost are top considerations and an HSM isn’t the best option. So how does one implement hardware security, while keeping cost and size down?
An Easier, More Effective Defense Against Counterfeiting
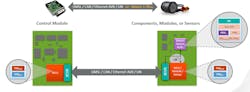
One proven method for preventing automotive counterfeiting is secure authentication (Fig. 1), which can support use cases such as:
- Safety and reliability to ensure that only OEM-approved components are connected to critical systems in the vehicle.
- Data integrity to confirm connectivity of genuine modules and sensors that only produce valid data.
- Secure boot for validating firmware installs to detect load errors and thwart the risk of malware attacks.
- Feature control for secure management of system features as subscription- or factory-based options.
From ADAS equipment to airbags to electric-vehicle (EV) batteries, the systems in a vehicle that could benefit from secure authentication are wide-reaching. With a secure-authentication IC, you can authenticate module and sensor combinations either remotely or locally.
Some OEMs are even going a step further and adding a deterrent to car part theft by implementing two-way authentication on high-value components that are more likely to be stolen. Two-way authentication means that if a component is stolen from a vehicle and placed in another car or system, the authenticator within the peripheral can block the part’s operation in this invalid system. A secure authenticator can help here by ensuring that vehicle components can’t be repurposed.
Another example where authentication is becoming more relevant is in lithium-ion battery systems. These highly efficient batteries are the primary choice of power supply for EV manufacturers. However, they have inherent safety implications and are costly. For these two reasons, a lot of EV manufacturers are concerned with ensuring that any battery replacement would block a counterfeit and potentially harmful battery from operating in the vehicle.
Protecting Automotive System Integrity
An example of a secure authenticator specifically designed to tackle the growing threat of automotive counterfeit components from infiltrating your automotive ecosystem is the DS28C40. It’s a small chip that can be embedded inside any automotive peripheral, such as a camera, sensor, EV battery, front-light module, etc. (Fig. 2).
The authenticator’s role within the peripheral is to prove to the ECU that the component is a genuine, OEM-approved part of the system. This is accomplished via elliptic-curve digital signal algorithm (ECDSA) cryptography, an asymmetric algorithm that relies on a certificate and a public-private key pair to validate itself to the host ECU module.
The advantage of asymmetric cryptography is that key management is easy to implement. The private key, which is unique to each authenticator, is securely stored in the DS28C40 and can’t be accessed externally. On the host ECU side, the public key is read from the authenticator, but like the “public” description suggests, it doesn’t need to be protected against discovery. The authenticator can be integrated into any automotive component at risk of being cloned, replaced, or stolen. For those who are new to security, knowing that there’s no need to worry about securing a key on the host side usually results in an audible sigh of relief.
Summary
As the automotive industry continues to incorporate more electronic components to deliver sophisticated new features with each generation of vehicle, one truth remains clear: Protecting human life remains paramount. What better way to do so than by making sure that the components responsible for making life-saving decisions haven’t been compromised?
Audrey Barber is Associate Business Manager, Micros, Security & Software Business Unit, at Maxim Integrated.
References
1. https://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/