The only thing harder than explaining what security really means is explaining security products and what they really mean. Security tends to be hard because it entails so many nuanced, yet important, details. Get something wrong and a system can be easily compromised.
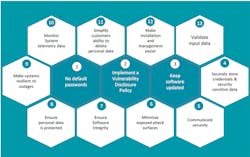
That’s why properly incorporating security into a product is important—and why it can be costly and confusing to implement. It’s also important to know what’s being secured and why a few systems require extreme levels of security. Likewise, it’s useful to know what the attack surface for a system will be and the type of threats that must be mitigated. A good starting point is to check out best practices for IoT security (Fig. 1).
Often, a developer has access to a range of security techniques, with software and hardware available. This includes writing code with as few bugs as possible as these can also be potential points of attack. Assembling all of the components from a security standpoint can include details like key management, secure-boot support, and encryption support in the form of standard protocols like Transport Layer Security (TLS). Unfortunately, doing this all from scratch can be time-consuming and error-prone, which is, of course, what you don’t want when talking about security.
Products like IAR’s Security from Inception Suite address the needs and education of developers when it comes to system security, especially for embedded devices. IAR is well known by embedded C/C++ developers for its IAR Embedded Workbench that includes features like MISRA C support.
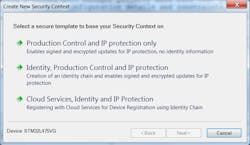
Security from Inception builds on the IAR Embedded Workbench, but the starting point is really the Embedded Trust security development environment (Fig. 2). With this tool, developers can define profiles that will eventually be using in the application and C-Trust, another tool that integrates security into the development process via the Embedded Workbench.
The Embedded Trust wizard is able to create a profile based on answers from a few questions. More advanced developers can enhance the profile based on a better understanding of the security requirements of an application and the organization that will build and manage the end product.
A typical security profile will include details like the cryptographic keys and certificates, secure-boot configuration, specifications for device security, the application update process and its associated policy, as well as device memory layout. Organizations that have a Corporate Information and Security (CISO) are likely to take advantage of these more robust configuration capabilities while many others will utilize one of the predefined profiles.
The C-Trust support is accessible from the IAR Embedded Workbench (Fig. 3). It uses the security profile developed or chosen using Embedded Trust. C-Trust handles details like secure-boot manager support for utilizing a hardware root of trust from the target platform. Automatic encryption and code signature support is part of C-Trust. It ties into the software key structure used by an OEM, so that security is part of the development process and not a later add-in, which rarely works out well.
C-STAT is an integrated static-code analysis tool that’s also part of the Security from Inception Suite. It helps to ensure that the application works correctly.
Another component in the Embedded Workbench is support for the Secure Desktop Provisioner (Fig. 4). This allows a target such as a secure microcontroller to be programmed with the application in the same fashion as it would on a production line.
The Secure Desktop Provisioner is part of the Advanced and Premiere editions of the suite. The Basic edition rounds out the suite. You can check the IAR website for details, but the Basic edition generally targets developers that would like to take advantage of the predefined security profiles. The amount of training and number of seats increases with Advanced and Premiere editions.
One key aspect of the suite is its integration into the development process—programmers can utilize a secure version of their application during development and testing of the software. The application code is ready for production deployment, which also includes security support that guarantees the code programmed in the factory is the one created by the developers.
Developers need to know about the keys and other artifacts and processes involved in building and managing security in the application as well as the development and deployment system. However, secure management of all these artifacts is handled by the suite, significantly reducing the amount of work needed to develop and deploy a secure system.
Security does need to start from project inception, and it must be ubiquitous throughout the development and deployment process. It doesn’t have to be a significant time sink if the right tools are employed.
About the Author
William G. Wong
Senior Content Director - Electronic Design and Microwaves & RF
I am Editor of Electronic Design focusing on embedded, software, and systems. As Senior Content Director, I also manage Microwaves & RF and I work with a great team of editors to provide engineers, programmers, developers and technical managers with interesting and useful articles and videos on a regular basis. Check out our free newsletters to see the latest content.
You can send press releases for new products for possible coverage on the website. I am also interested in receiving contributed articles for publishing on our website. Use our template and send to me along with a signed release form.
Check out my blog, AltEmbedded on Electronic Design, as well as his latest articles on this site that are listed below.
You can visit my social media via these links:
- AltEmbedded on Electronic Design
- Bill Wong on Facebook
- @AltEmbedded on Twitter
- Bill Wong on LinkedIn
I earned a Bachelor of Electrical Engineering at the Georgia Institute of Technology and a Masters in Computer Science from Rutgers University. I still do a bit of programming using everything from C and C++ to Rust and Ada/SPARK. I do a bit of PHP programming for Drupal websites. I have posted a few Drupal modules.
I still get a hand on software and electronic hardware. Some of this can be found on our Kit Close-Up video series. You can also see me on many of our TechXchange Talk videos. I am interested in a range of projects from robotics to artificial intelligence.