IoT Device Security: Getting Started
This article series is in the Improving Software Code Quality topic within our Series Library
What you'll learn:
- Developing a security plan for IoT, including "out of the box" solutions.
- How to incorporate the standards and legislation enacted to combat security issues into current systems.
- Choosing the right tools to implement your security plan.
Security is critical to enabling devices to work together in trusted networks, share personal data within a network, and enable private operation with cloud services. Similarly, a secure foundation is required to manage updates and procure additional services.
Furthermore, IoT device vendors are realizing that the value of their IP equates to the value of their company. The possibility of IP theft is very real. In fact, the European Union estimates it may be as high as $60 billion per year according to the latest research. In addition to the financial implications, this level of IP theft has a potential impact of nearly 300,000 jobs in the EU alone.
Implementing security from inception not only secures applications and data, but also IP, the supply chain, jobs, and ultimately the global economy.
As mentioned, cost has always been a concern when it comes to adding security. However, it doesn't have to be an expensive proposition. It’s possible to lockdown an existing mainstream device to ensure that the IP can’t be extracted or that rogue code can’t be injected. The cost of this baseline level of security ranges from zero to extremely low.
Of course, additional effort is required to develop and test a secure device and produce it in a manner that ensures IP can’t leak. Even so, the total cost of security should be less than 1% of the cost of the end device.
Every day, it seems like there are more secure chips coming to the marketplace that developers should examine rigorously. For example, the Secure Firmware Install (SFI) technology, in the latest devices from STMicroelectronics, is a tremendous step forward for secure manufacturing.
Similarly, the implementation of secure enclaves such as the Renesas Trusted Secure IP (TSIP), secure information far better than previously possible. Additionally, new security technologies integrated into mainstream devices, such as the physically unclonable functions (PUFs) in the NXP LPC55S family add significant protection.
From a development perspective, security can have a major impact. However, with better “security out of the box,” such as Embedded Trust and IAR Systems C-Trust, most of the heavy lifting is already complete. This allows developers to focus on their applications rather than on the intricate details of security.
To achieve that, security must be included at the beginning of the development process with the concept of a secure context, or profile, which defines how security is implemented across an organization’s products. This approach makes security painless and fast, and it minimizes costs.
Standards and Legislation
Consumer protection is driving standards and legislation globally. For example, consumer electronics products shipped into Europe now must meet the European standard EN303645. In addition, IoT devices are subject to the privacy legislation outlined in the GDPR regulations.
Within these regulations lies an unequivocal requirement to keep personal user data secure and to ensure it can be erased at a product’s end-of-life, or when it’s sold or passed on. Similarly, any data supplied as part of a service, even something as straightforward as voice control of a coffee machine, falls within the auspices of this legislation. GDPR established clear penalties for breaches, with a minimum fine of €10 million, which can escalate to 4% of company’s global revenue if the company is found to be purposefully delinquent.
The goal is to motivate companies to demonstrate that they have met the security requirements either with a formal process, such as Arm PSA, or a self-certification process like the IoT Security Foundation’s Conformance Framework. This makes sense as an easy first step for every organization.
For example, IAR Systems and Secure Thingz recently announced its Compliance Suite. It provides developers and organizations with the security development tools, practical guidance, and knowledge needed to rapidly build applications that are compliant with security legislation.
In the United States, laws in California and Oregon have brought security considerations to the forefront of design. The challenge for most developers is understanding what’s meant by “reasonable” vs. “unreasonable” security features. More specificity is required for the laws to be effective.
At a minimum, reasonable security should require companies to show an analysis of the risk profile and attack surfaces of a device. For most IoT applications, reasonable security may mean an attacker can only compromise a specific device if they have physical access. It’s the ability to carry out class breaks, or compromises of all attached devices, that carries the highest risk.
In addition to California and Oregon, the IoT Cyber Security Improvement Act was signed into law in the United States in December 2020, and more recently the Executive Order for Improving the Nation’s Cybersecurity, often reduced to Software Bill of Materials, has been introduced. The challenges, much as we have seen in Europe, California, and Oregon, resolve around what’s defined as a “must have” for security, versus the “nice to have.”
Fortunately, the frameworks in the UK and Europe have evolved and now provide a good framework of “good, better, best,” which fits well into the IoT Cybersecurity Improvement Act and the work that NIST is doing to implement the Act as technical policy. The EN 303645 standard has three or four core requirements that are the “must haves.” The remainder represent best practices that organizations should know and target.
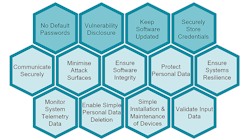
The four core requirements are simple to present but still complex in the implementation. They are:
- The need to implement cryptograph authentication to avoid fixed passwords and enable the migration to more robust identity—a bedrock of trust across IoT devices.
- The requirement to disclose vulnerabilities to customers, with clear communication of the support, update, and patching agreement.
- The obvious need to release updates that must be delivered securely and be sufficiently simple for a consumer to install.
- The requirement to ensure provisioned credentials and private data are robustly protected within the device—ensure privacy for the user and protection against class attacks.
While legislation and standards are starting to impact the marketplace, a significant lack of knowledge and experience is slowing the process. Organizations who understand security is a critical differentiation are moving quickly, now that there’s a clear set of standards.
For example, the largest shipper of connected lights, or lumens-as-a-service, has adopted a security-first methodology for the hundreds of millions of devices shipped every year. While there will be laggards, in the next two years we will see significant changes. This will be augmented by increased consumer marketing awareness and a more level playing field in Europe, the United States, and large parts of Asia-Pacific.
Implementing Security
Security must come from the top of any organization, with leadership playing a major role, and COOs and CISOs being responsible for both inbound IT threats and the security of their own products. These stakeholders are critical in defining the organization’s security profile, and ensuring common standards for product update support, patching, and customer management. The engineers can implement the technology, but creating corporate policy starts at the top.
At IAR Systems and Secure Thingz, we’ve worked with many organizations to create standard, but flexible, security contexts. This enables organizations to quickly adopt a standard model for identity, authentication, updates, and management of devices, either via a cloud provider or direct, and subsequently tune it to their specific needs. This process once took months to resolve. Now, though, it be completed in less than a day, providing a clean framework for the engineers to build upon using the standard development tools they know and trust.
Of course, not every organization has a gold standard functioning CISO. In these cases, the policy is often delegated to the engineers. Most embedded engineers are extremely capable, but they need more information around several areas of security. These include:
- Best practices for designing a secure IoT product
- Interpretation of standards
- Basic information on standards
With this, adopting standard policies that meet many of the requirements for EN 303645 will make their jobs significantly easier.
Security impacts every aspect of how a device operates over its lifetime. Understanding the context for the standards is important. However, even the most talented engineers must focus on getting products completed and into manufacturing.
Getting Up to Speed
Therefore, for most organizations, a clear understanding and interpretation of the standard is important in knowing what tools are proper to achieve their goals. Getting educated quickly is important, and new resources, such as the training in IAR Systems’ on-demand IAR Academy courses, can help close the knowledge gap.
In addition, engineers should read the IoT Security Foundation guidelines or attend online training on the guidelines and compliance frameworks, which are free to access. Furthermore, the EN 303645 standard is freely available online, and while a little dry, does identify the 13 best practices with individual requirements.
Once educated, the next goal is to understand the need to protect key assets from the potential bad actors across the globe. Although consumer electronics is less likely to be subject to the pervasive state-sponsored attack, it’s probable that smart homes could be held to ransom—especially on very cold days when heating is a necessity.
Implementation Essentials
The next step is to look at implementation. There are two or three major stakeholders here: the silicon platform, the tools, and potentially the cloud. The silicon platform is simple. Does the chip have the security features needed? If this is a simple application, then existing mainstream devices can be made somewhat secure by disabling the debug ports and installing secure boot frameworks. More advanced devices offer leading-edge cryptography, secure enclaves, and integrated TPMs.
The tools are critically important in supporting implementation. Here new tools such as Embedded Trust and C-Trust make a significant impact, reducing the overhead of implementing security from months to hours. Finally, there may be a desire to connect to the cloud, and of course credentials need to be provisioned, either in manufacturing or once connected.
The biggest single aspect an engineer can focus on is to presume every device is, or will be, compromised. This slightly negative perspective is critical in starting the journey to a more secure IoT, as it drives the implementation of a root of trust with properly encrypted and signed updates.
If engineers presume the device will be compromised, they will design a safe space for recovery, to regain control of the device and remediate with patches and updates. This is achievable with most microcontrollers on the market already, so the cost is minimal, but the benefits are huge. Again, modern tools will now implement these frameworks for the developer, with simple configuration and unlimited flexibility. Thus, security is easily within every engineer’s reach.
Ultimately the goal is to ensure the product is compliant, demonstrating that common attack vectors have been thought about and closed off, and that the four core requirements have been met. Once this is achieved, the industry will have taken a significant step toward a secure IoT.
Read more articles in the Improving Software Code Quality topic within our Series Library
About the Author
Haydn Povey
Founder and CEO, Secure Thingz/General Manager Embedded Security Solutions, IAR Systems
Haydn Povey is the Founder and CEO, Secure Thingz/General Manager Embedded Security Solutions, for IAR Systems, a company that supplies future-proof software tools and services for embedded development, enabling companies worldwide to create the products of today and the innovations of tomorrow. Mr. Povey also currently sits on the Executive Steering Board of the IoT Security Foundation.
Mr. Povey has been in senior management at leading global technology companies for over 20 years, including 10 years in senior marketing and business development roles at Arm. While at Arm, Mr. Povey most recently looked after the company’s strategy and product roadmaps for security within IoT and M2M marketplaces, and he led the development and introduction of the Cortex-M microprocessor family.