FPGA-Based Security Platform Thwarts Firmware Attacks
What you’ll learn
- The types of attacks target embedded systems at the boot level.
- How Lattice Sentry uses RISC-V to address the problem.
- How to monitor and intercede I2C and SPI memory interfaces.
- How a modular design can secure multiple embedded processors within a system.
Lattice Semiconductor announced two significant security solutions. Lattice Sentry is an FPGA-based solution that easily can secure multiple processors and other logic using a single chip. And the SupplyGuard service is its part management system that provides secure ownership management and transfer that doesn’t require exposing secret keys to partners and customers. Together they’re designed to deliver a secure, end-to-end supply chain that supports dynamic trust.
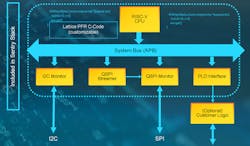
Lattice Sentry is actually a design framework built around the Lattice Propel design tool, the MachX03D FPGA, and the Lattice Sentry software and FPGA IP. It’s built to provide a secure management system for multiple devices from microcontrollers to processors and almost any device that utilizes a serial flash memory with an SPI or I2C interface. This is done by monitoring the communication between the devices and their storage (Fig. 1).
The custom code and IP on the FPGA can passively monitor or sit between a storage device and its host. Thus, Lattice Sentry can detect attacks and take actions to thwart attackers through various means depending on the application and system configuration. This might mean resetting a processor or reprogramming the memory. The FPGA typically has ties to the memory and the host and possibly other devices.
A number of scenarios are possible for managing security, from simply watching memory traffic to checking boot code before it’s used. One way to do the latter is to have a switch sit between the host and the other devices. This would allow the FPGA to examine the contents of the serial device before the host boots using the program in the memory device. The contents are authenticated against secure keys within the FPGA before the host can use the memory contents. If an error is detected, then the FPGA can replace the code with a backup or perform other chores while preventing the host from booting.
The number of scenarios and configurations is vast and application-specific. The solution is applicable to configurations with a single microcontroller, or to systems with multiple processors where the boot sequence needs to be controlled.
Although the systems are designed for memory operations, these serial interfaces are often used for peripherals as well. It’s not beyond realm of possibility to manage and control devices where one might limit functionality based on various states and settings. This would require additional programming and design, but it may be particularly useful in applications where some devices that should be secured don’t have the capability to do it themselves.
Each implementation will be a custom job, so there’s no preprogrammed off-the-shelf chip. The job of designing, implementing, and testing is simplified using the drag-and-drop configurator within Lattice Propel, as well as the predefined modules for managing and monitoring the serial memory interfaces. Custom IP can be designed to handle new configurations as well as control of the hosts.
The Lattice Sentry architecture is built around a soft, RISC-V core (Fig. 2). The number and types of serial interfaces, switches, etc. will depend on the application, but a single FPGA can deal with multiple devices simultaneously. Software running on the RISC-V core will not usually track memory traffic in real time. This is something the rest of the FPGA can handle in parallel. The software can make tasks easier to perform, such as authenticating the contents of memory before allowing a host to boot.
Typically, a single chip will be needed even when multiple devices are utilized, although it’s possible to use multiple chips to take on very large systems. These could cooperate with each other; however, this is something a designer would have to consider and employ.
Lattice’s chips are designed to be secure with on-chip storage and security mechanisms to prevent attacks on itself. As a result, the chip can keep secrets that could be applied to manage the other parts of the system.
Securing the Supply Chain
The Lattice Sentry includes on-chip keys, a unique ID, and its own secret key. Consequently, it’s able to accept additional keys that it stores internally for use with a variety of features, including verification of memory as mentioned earlier. Such support can also be used to manage ownership and control of the device as it moves through the supply chain. This is where the Lattice SupplyGuard service comes into play (Fig. 3).
Lattice SupplyGuard is designed to start with manufacturing and go throughout the lifetime of a product. It can be employed to prevent counterfeits as well as stop third-party manufacturing services from building more parts than ordered, which in turn might be sold on the grey market.
The service takes advantage of Lattice Sentry’s ability to manage its own keys, which can be used to authenticate and utilize services based on its programming. The complexity of the supply chain and the product design means that many will want to take advantage of Lattice’s support services to design both the Lattice Sentry-based devices, as well as how they’re integrated into the supply chain.
About the Author
William G. Wong
Senior Content Director - Electronic Design and Microwaves & RF
I am Editor of Electronic Design focusing on embedded, software, and systems. As Senior Content Director, I also manage Microwaves & RF and I work with a great team of editors to provide engineers, programmers, developers and technical managers with interesting and useful articles and videos on a regular basis. Check out our free newsletters to see the latest content.
You can send press releases for new products for possible coverage on the website. I am also interested in receiving contributed articles for publishing on our website. Use our template and send to me along with a signed release form.
Check out my blog, AltEmbedded on Electronic Design, as well as his latest articles on this site that are listed below.
You can visit my social media via these links:
- AltEmbedded on Electronic Design
- Bill Wong on Facebook
- @AltEmbedded on Twitter
- Bill Wong on LinkedIn
I earned a Bachelor of Electrical Engineering at the Georgia Institute of Technology and a Masters in Computer Science from Rutgers University. I still do a bit of programming using everything from C and C++ to Rust and Ada/SPARK. I do a bit of PHP programming for Drupal websites. I have posted a few Drupal modules.
I still get a hand on software and electronic hardware. Some of this can be found on our Kit Close-Up video series. You can also see me on many of our TechXchange Talk videos. I am interested in a range of projects from robotics to artificial intelligence.