Mike's Blog: Staying vigilant about cybersecurity during the government shutdown
As of this morning, the United States is in its 27th day of a partial government shutdown—the longest such shutdown in U.S. history. Government shutdowns aren't rare—there's been 21 gaps in funding for the federal government since 1976—but this one has unfortunately set a new mark for longevity. The previous longest was a 21-day shutdown from December 1995 to January 1996 during President Bill Clinton's tenure.
Now, I'm not going to get into the politics of the current partial government shutdown, mainly because I'm not in a position to speak on it. But I'm sure we can all agree that it's a bad situation. I'm sure anyone reading this blog knows someone who works for the government and has been negatively impacted by the situation. We know that some 800,000 federal workers have either been furloughed or are currently working without pay.
The shutdown's impact on the U.S. economy appears to be growing, as a White House official stated Tuesday that the ongoing funding gap is shaving 0.13 percentage points of quarterly economic growth each week.
Tens of thousands of those furloughed employees have been called to return to without a paycheck due to the risks upon agencies working understaffed, such as aviation safety inspectors or the IRS as it heads into tax season.
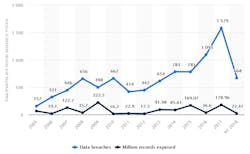
Another area of concern in this shutdown that doesn't seem to be receiving much attention is cybersecurity. The rate of cybercrimes has grown significantly over the past decade as the Internet has matured, and especially over the last few years. A recent Statista report found that in 2015 the U.S. saw 781 data breaches; 1,093 data breaches in 2016; 1,579 data breaches in 2017; and 668 data breaches in the first half of 2018.
One would think a government shutdown would be a prime opportunity for cyberattacks upon federal agencies, contractors, or other companies that do business with the government.
International law firm Dorsey & Whitney commented: "As the impasse threatens to drag on indefinitely, private sector impacts are increasingly likely in the cyber area. Companies need to assess how their vulnerability has been affected with the absence of key Department of Homeland Security resources, especially in areas involving critical infrastructure Systems, as well as federal regulatory watchdogs in the financial and health care spaces."
On this subject, Dorsey & Whitney offered commentary from firm partner Robert Cattanach, who has previously worked as a trial attorney for the U.S. Department of Justice and was also special counsel to the Secretary of the Navy. Today he practices in the areas of regulatory litigation, including cybersecurity and data breaches, privacy and telecommunications, civil and criminal enforcement proceedings and international regulatory compliance.
Here is Cattanach's advice for companies during the shutdown when it comes to their cybersecurity:
So what is a company concerned about its increased exposure to do?
- First, assess your cyber vulnerability with a fresh set of eyes. Cyber thieves thrive when environments that rely on careful cyber maintenance and monitoring from different sectors suddenly are denied that critical set of second eyes. Consider another resource, perhaps outside consultants or industry-specific subject matter experts, to role-play what federal cyber regulators might otherwise have been doing.
- Second, double down on internal processes and controls. Ultimately, we are only as good as the monitoring that we can do, which is never perfect. Yes, IT is always clamoring for more resources, and mission-creep is a common problem, but temporary enhancements in the areas of system monitoring and access controls may be well worth the temporary pain on the balance sheet, especially when compared to the alternative.
- Third, remember not only that: “it ain’t until it’s over”, but almost certainly sometime well after that. Cybercriminals are a patient lot. Most intrusions occur well before the intruder actually executes on them. Long after the shutdown has ended, and of course it will, companies will face the risk of ‘cyber sleeper cells’ embedded in their systems during a time when those systems were marginally more vulnerable, and then activated weeks and months from now when vigilance may have subsided,
These are not one-size fits all suggestions. Each company can, and should, do a fresh assessment of how the shutdown might be increasing their cyber exposure, document that assessment and what was done about what was learned, and be ready to use that assessment as evidence of good faith and due diligence in the event that cyber criminals or nation states used this time to advance their causes, potentially at your expense."
Stay vigilant out there, EE readers, and let's hope this shutdown ends as soon as possible.