RISC-V Serves Up Open-Source Possibilities for the Future
This article is part of the TechXchange: RISC-V: The Instruction-Set Alternative
What you’ll learn:
- What is RISC-V?
- The basics of RISC-V.
- Applications and uses of RISC-V.
RISC-V is described as an open standard instruction set architecture (ISA) that's based on the reduced instruction set computer (RISC) principles. Boiled down, RISC simplifies the instructions given to the processor to accomplish tasks. However, unlike most ISAs, RISC-V is provided under open-source licenses, meaning anyone can contribute to its development and it doesn't require fees to use.
Every processor utilizes an ISA to function along a set of prescribed parameters, and almost all of them are proprietary. Though some are licensable, very few are available for free, which makes RISC-V unique in that anyone can use the instruction set to develop their own processors.
Developed at Berkeley in 2010, the instruction set offers a variety of advantages, including its openness, simplicity, clean-slate design, modularity, extensibility, and stability—unlike legacy ISAs that are decades old and can't handle the latest compute workloads. The idea was to remove the complexity in designing processor cores, which has evolved into a software-visible interface for myriad implementations, including embedded systems and supercomputers alike.
At its core, RISC-V provides a description of how processor design should function, essentially a descriptive base on how software communicates with a processor. RISC-V presents a level of flexibility to design new processors. That’s because the instruction set isn’t defined at the ISA level, but rather is the compilation of the processor and other design parameters. Thus, engineers and makers can quickly implement a minimal instruction set, along with well-defined and custom extensions, to design processors for next gen workloads.
RISC-V also leverages established and common IP building blocks with the development of the maker community's growing set of shared tools and development resources. Contributions from the user base reduce costs associated with R&D and accelerate time to market, adding to the set's overall efficiency.
Modular Design, Bases, and Extensions
The RISC-V instruction set is modular by design, meaning users can customize the platform and drop in any extensions they require. The ISA bases and their extensions are developed collectively between industry, researchers, and educational institutions.
Broken down, the ISA cores provide specified instructions (and coding), control flow, registers, memory and addressing logic manipulation, and ancillaries. Alone, RISC-V can implement a simplified general-purpose computer with full software support, including a general-purpose compiler.
As of now, four base ISAs are characterized by the width of the integer register and the corresponding size of the address and by the number of integer registers. Two primary base ISAs correspond to the 32- and 64-bit address spaces, which are RV32I and RV64I, respectively. In addition, a subset variant, RV32E, is equipped with half the number of integer registers and designed for small microcontrollers.
All base ISAs have differentiating features that can be employed for a particular use case. However, they’re separated to optimize each without the need to support the operations of the others.
To better understand the combinations of functions that may be implemented, an extensive reference was devised to define and specify each, which are outlined in Chapter 27 of the current ratified Unprivileged ISA Specification. The instruction set base is specified first, followed by coding for RISC-V, the register bit-width, and the variant.
Letters specifying implemented extensions come after the set base. Each letter can be followed by a major, optionally followed by "p," and a minor option number. It defaults to 0 if a minor version number isn't utilized and 1.0 if all of a version number is absent.
Thus, RV64IMAFD may be written as RV64I1p0M1p0A1p0F1p0D1p0 or simplified as RV64I1M1A1F1D1. Underscores may be used between extensions for easy readability, e.g., RV32I2_M2_A2. The terminology becomes even more extensive when multiple extensions are added.
Once the base is decided, users can add those extensions to define the exact rules of the core. Extensions currently open and ratified include:
- M: Standard Extension for Integer Multiplication and Division
- A: Standard Extension for Atomic Instructions
- F: Standard Extension for Single-Precision Floating-Point
- D: Standard Extension for Double-Precision Floating-Point
- G: Shorthand for the Base and Above Extensions
- Q: Standard Extension for Quad-Precision Floating-Point
- L: Standard Extension for Decimal Floating-Point
- C: Standard Extension for Compressed Instructions
- B: Standard Extension for Bit Manipulation
- J: Standard Extension for Dynamically Translated Languages (C#, Java, Haskell, etc.)
- T: Standard Extension for Transactional Memory
- P: Standard Extension for Packed-SIMD Instructions
- V: Standard Extension for Vector Operations
- K: Standard Extension for Scalar Cryptography
- N: Standard Extension for User-Level Interrupts
- H: Standard Extension for Hypervisor
- S: Standard Extension for Supervisor-level Instructions
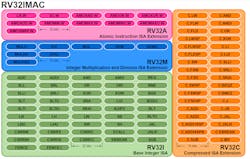
Now that we have an overview of the extensions, let's look at a practice example and decode how a GD32V with an RV32IMAC (see figure) core breaks down: GD32V is a 32-bit RISC-V core (RV32I) with integer multiplication and division (M), atomic instructions (A) and compressed (16-bit) instructions (C).
Shown is the complete RV32IMAC instruction set. (Image credit: Eduardo Corpeno, Creative Commons Attribution-Share Alike 4.0 International via Wikipedia)
Another example could be Kendryte's K210 dual-core RISC-V RV64IMAFDC/RV64GC SoC (system-on-chip). When broken down, it translates as a 64-bit RISC-V processor (RV64I), with integer multiplication and division (M), atomic instructions (A), single-precision (F) and double-precision (D) floating-point (I + M + A + F + D = G), along with compressed instructions (C).
Although the list is already extensive, a situation may arise when no suitable ready-made ISA extension fits the design needs. In these cases, the RISC-V specification allows for adding a custom ISA extension. This can be the engineer's or maker's specific integration and a key differentiator.
Because of the unique nature of the RISC-V ecosystem, custom ISA extensions won't break compliance with the main specification. Even with additional instructions, the processor is still fully RISC-V-compliant and can run a generic software stack garnered from the ecosystem.
Applications and Future Development
Many companies are taking advantage of RISC-V to create custom processors designed to handle newer technologies' power and performance requirements, including artificial intelligence (AI), the Internet of Things (IoT), and virtual and augmented reality (VR/AR). RISC-V also is being used for custom processors targeted at applications from edge computing to cloud servers and high-performance computing (HPC). Moreover, companies are slowly rolling out RISC-V for general-purpose processors to be used in laptops, desktops, and data centers with vertical and horizontal scaling.
SiFive, a company dedicated to producing RISC-V hardware, has produced several processors designed to handle maximum throughput and extensive workloads. These range from 8-stage, dual-issue, in-order architectures equipped with 256-bit vector engines to advanced out-of-order processors, including the P650, P550, and P270. These were produced to offer direct competition to the Arm Cortex ecosystem found in many mobile devices and development boards.
Hard-drive companies, including Western Digital and Seagate, are implementing RISC-V in their next-gen storage solutions for data-centric and security-critical applications.
According to the RISC-V International Foundation, about 600 members signed on to bring about RISC-V-enabled hardware in 2010, and that number has ballooned to over 2,400 over the last decade. They also expect the adoption of RISC-V over the entire CPU spectrum, including enterprise and consumer markets, by 2025.
A number of companies and academic institutions are currently developing RISC-V-based processors that are expected to be released in the coming years, including ATSC, Cambridge, Esperanto Technologies, ETH Zurich, NVIDIA, and more. While current RISC-V technologies can't currently compete with x86 offerings from AMD and Intel, there’s enough momentum for the open-source instruction set architecture to produce competitive hardware in the near future.
Read more articles in the TechXchange: RISC-V: The Instruction-Set Alternative.
About the Author
Cabe Atwell
Technology Editor, Electronic Design
Cabe is a Technology Editor for Electronic Design.
Engineer, Machinist, Maker, Writer. A graduate Electrical Engineer actively plying his expertise in the industry and at his company, Gunhead. When not designing/building, he creates a steady torrent of projects and content in the media world. Many of his projects and articles are online at element14 & SolidSmack, industry-focused work at EETimes & EDN, and offbeat articles at Make Magazine. Currently, you can find him hosting webinars and contributing to Electronic Design and Machine Design.
Cabe is an electrical engineer, design consultant and author with 25 years’ experience. His most recent book is “Essential 555 IC: Design, Configure, and Create Clever Circuits”
Cabe writes the Engineering on Friday blog on Electronic Design.