IoT Security Getting Well-Deserved Attention
There is no doubt that security concerns are heightening in the quickly growing Internet of Things (IoT) world. The public is reminded almost daily that the internet can be compromised with an array of consequences, much of which they don't really understand. Yet, consumers unwittingly encourage hacking by putting so much of themselves on the grand network, with their incessant use of smartphones and social networks, let alone buying some of those IoT devices or just driving around in modern automobiles. Business faces much greater risk, threat, and financial impact from security breaches, yet simply cannot operate without the digital electronics that expose them to it.
The electronic products and digital services that we normally use are revered for the functions they perform and maybe how easy they are to use or how cost-effective they are. The system designers see their creations that way, too. How reliable and secure those systems and that software may be is difficult to assess and tends to be pretty low on the priority list, spiking up only when a problem suddenly becomes traumatic.
Users have trusted that the engineers and programmers have created very useful products and services, regardless of whether they understand the underlying complexities of how they work, but that they are safe as well. Government agencies may establish regulations to assure a certain level of safety, but the digital world spins much faster than policy advances. Also, governments can be part of the problem and a newfound nationalism is throwing suspicion on other governments' motivations as well.
Ultimately, the designers of our modern electronic systems and digital services must continue in their role of responsibility for building the best products they can while being good stewards for their safety and security. Unfortunately, there are growing numbers of people intent on devising new ways to circumvent established preventative measures, so staying on top of security is a never-ending task.
The path forward to security in the highly connected Internet of Things (IoT) world is still being blazed. It is good to periodically review how different approaches to security have progressed.
Intel, CISCO, and Amazon may have schemes for the internet side of things, but Arm and many semiconductor companies are executing on strategies to tighten up security on the “things” side as well. The IoT is and will be well-served by Arm-based products, so Arm's efforts in security are important, if only from a holistic view. There are many semiconductor providers with an interest and a hand in IoT security, but a representative company like Microchip can give insight where the rubber meets the road.
Bearing Arms in Defense
Security was a predominant theme at the recent Arm TechCon in Santa Clara, Calif., where Arm Ltd. highlighted its new Platform Security Architecture (PSA). With the Arm processor architecture being used by essentially every microprocessor (MPU) vendor and many microcontroller (MCU) vendors in the industry, any reasonable program promoted by Arm is sure to quickly gather a large following. Arm processors' defacto position in mobile phones, tablets, and what eventually became the IoT has given Arm a healthy heads-up of the issues of security.
Arm has posted a "Security Manifesto" with a handful of luminaries highlighting security issues, giving cues from other systems (including human and biological), and calling on equipment makers and service providers to take threats to cyber security seriously and to provide a safe environment in which connected digital equipment can operate. Arm, rightfully, sees security as a responsibility of such businesses. However, specifics are limited and Arm believes "industry bodies" will pull together actual standards.
Platform Security Architecture
A centerpiece in Arm's security position is the Platform Security Architecture (PSA), better addressing the security challenges all the way down to the smaller, cost- and performance-constrained critical components of systems—MCUs. Of course, the highest volume of processors is in MCUs, so it is vital that data flowing up from and managed by these workhorses is not compromised and that MCUs do not become access points by which the larger system, or even unrelated systems, can be attacked or infiltrated.
However, the PSA also addresses higher-performance systems and even initially specifying support for the Arm v8-A architectural profile, as well as Arm v8-M, which could be adopted to the Arm v7-M and v6-M. PSA material is littered with exotic terms, acronyms, and explanations that take some getting used to—or leave it all to the security wizards—something the concept was supposedly trying to avoid.
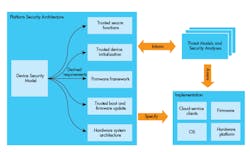
There are three main parts to the PSA. These are given as follows:
- Threat models and security analysis, derived from a range of typical IoT use cases
- Architecture specifications for firmware and hardware
- An open-source reference implementation of the firmware architecture implementation
(source: Arm, Ltd)
The first is a set of models or use cases that typify many applications with an analysis of the security threats they may face and the potential consequences of an attack. This may be used to judge or qualify the protection that a given application affords. The models feed issues and urgency to the protective specs being developed.
A Device Security Model (seen below) describes the architecture. The implementation of such specs push all the way down to assuring that the silicon manufacturing processes are secure. This sounds like just any ol’ fab may not be qualified for producing tamper-proof security. When security is truly important, everything must be treated as suspect and as a potential weak link until demonstrated otherwise. Not only must initial device keys and attributes be secure, but later firmware updates, crypto certificates, and maintenance and calibration changes must be authenticated.
The PSA consists of three parts: the Threat Models and Security Analyses, an architecture specification for firmware and hardware, and an open-source reference implementation.
The PSA also lays out the elements that reside in secure partitions of the system (in the Secure Processing Environment) under hardware enforcement by the Secure Partition Manager, which probably makes the old memory management unit (memory protection unit in Arm parlance) look pretty rudimentary and narrowly focused.
The PSA builds from Arm's earlier TrustZone, Trusted Execution Environment, Trusted Boot, Root of Trust, SecureCores, and other protection elements.
Arm sees chip designers cordoning off security "enclaves" containing the most critical security elements as part of a larger silicon die. Arm is developing its own such intellectual property (IP) to be tagged CryptoIsland-300. That may sound like the place where John McAfee is fighting with his neighbors and hiding under the sand from satellite cameras, but the sand making up Arm's islands will be much more highly refined, intended to have rigid security on par with that found on SmartCards (chip-enabled bank cards and ID cards).
CryptoIsland details quickly become mind-boggling and complex. However, they also should reaffirm humanity's trust in things like our bank cards. Many features described on these CryptoIslands remind this analyst of all the precautions, lessons, technologies, processes, and solutions that semiconductor vendors have learned over decades in securing memory, processors, and chip cards from natural (alpha particles) and semiconductor-scaling-induced quality and failure problems, as well as code-, circuit-, IP-, and design-stealing protection practices.
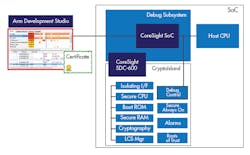
Arm also offers a Secure Debug Channel, the SDC-600 IP (below), which authenticates prodding into the silicon hardware under the guise of a debugger.
Arm’s SDC-600 Secure Debug Channel authenticates the host debugger using certificates before anything gets control of the CPU.
The third part of the initial PSA will address firmware (largely code) strategies including partitioning into secure and non-secure spaces with a Firmware Framework that eases reuse of code across various MCU cores and reliable updates.
Overall, the Platform Security Architecture is a work in progress, but lays out the greater structure that partners, chip vendors, OEMs, programmers, development-tool third parties, and application developers can gather around, work together on, and align their products and software to. It is an evolving program just now seeing the light of day, though it has obviously had a lot work put into it. Perhaps close partners have a much better understanding of how the concepts will play out in practice—silicon implementation, OS integration, coding techniques, system integration, and how well the PSA will work up the value chain—or is it the internet/Ethernet/wireless mesh—to the servers, databases, and cloud services.
As with all such schemes, it will take a long time for large-scale implementation to prove out. With more creative attacks being attempted every day, this will be a never-ending race. But at least Arm has the ear of the bulk of processor vendors and the third parties behind them, including and especially on those with customers building "things," diverse as they are, so Arm's PSA should have enough interested parties to steer it to success in securing the IoT.
Arm expects the PSA to lower the cost and time for its partners to design a secure system while lowering the risks of attack, hopefully using techniques that others in the industry also use, leading to an overall much-safer internet (of things). Perhaps, more realistically, application developers can more easily design a system that is an optimally secure system, providing sufficient security without costing too much to design, pilfering too much processor performance, or requiring too many additional resources (circuitry, memory, coding, delay…).
Microchip Pay-as-you-Go Security
One of the leading microcontroller suppliers is Microchip Technology, which has a more feet-on-the-street approach to serving security needs, probably more typical of semiconductor vendors. In spite of its $4 billion size, Microchip's business is almost wholly associated with MCUs. Most of its MCUs use its proprietary PIC architecture, although Microchip took a unique path in its 32-bit offering by utilizing the MIPS architecture (which seems to now be nearly a proprietary architecture). Microchip did pick up the proprietary AVR architecture and the ubiquitous Arm architecture when it bought Atmel.
Alongside the MCUs, Microchip has acquired and developed assorted networking and radio components with numerous communications peripherals on its MCUs. Associated with networking and especially RF, the company has picked up security components as well.
For security support, Microchip offers a selection of components to serve a variety of designers with widely different or changing needs. As it does for its MCU customers, Microchip provides easily accessible tools to help even less security-savvy customers to build in the level of security they need.
The security components are primarily add-ons that support the MCU, limiting the incremental expense to only those applications that need the security benefit. In conjunction with all of those MCU architectures, this makes good sense since every cent counts in small systems and Microchip is known for squeezing every penny of cost out of its products.
Microchip has products for authentication, RSA security, secure E-squared PROMs, TLS support, RNGs, unique serial numbers, ECC accelerators, crypto accelerators, and RFID chips. There are two Arm-based microcontroller families designed to be secure, with hardware crypto accelerators, secure boot, and on-chip facilities ideal for building point-of-sale terminals.
When it comes to end-to-end network security, Microchip helps designers with what it calls "Zero Touch Secure Provisioning," which is supposed to be easy enough that even an analyst can connect an IoT device to the Amazon Web Services cloud in full compliance with Amazon's regulations.
Rights, Privacy, Security: A Fine Line
Society has a struggle, debating and pushing the line of who has which rights, what is private, and when has security been compromised. Individuals, organizations, corporations, countries, and even softer concepts play into the discussion like culture, morals, deceit, and what is right. The arguments arise, develop, reconcile, and rehash over time. Often money is the ultimate resolution, but that has moral considerations, too.
Without trying to settle where lines of rights, freedom, and privacy should be drawn, security is about enforcing those lines. That enforcement has a cost, but security must be incorporated into our evolving inventions or they will fail from its absence. There will continue to be a learning process because the attackers will not stop trying. But one must determine a strategy, execute a rational plan, review real-world results, and make adjustments in order to advance to higher security.
The number of electronic devices and digital services in the world today, the interconnectivity of those devices, services, and humans, the sheer volume of network traffic, and the dependence of modern society on all those inventions pushes the importance of security in our digital world to where it cannot be ignored.
About the Author

Tom Starnes
Analyst
Tom Starnes is arguably the best-known embedded processor analyst in the semiconductor industry. Covering a range of products, Starnes' insight, coupled with his no-nonsense approach to processor and end-use analysis has led to his becoming one of the most sought-after consultants in the world of processors. It is through his hard-hitting insights that many key players in this industry have found their focus and refined their product strategies.