Being physically fit is a good thing, and fitness trackers like those provided by Strava can help people keep track of their workouts, and even where they were at the time. Strava is not alone in capturing and using this information. There is a plethora of wearable tech, ranging from Fitbits to Apple Watches, that tracks not only location, but also activity and heart rate. There is a lot of information that can be garnered from sensors in these devices.
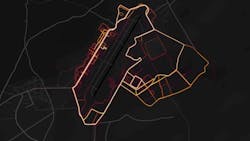
The latest news is that Strava provided aggregate fitness tracker information in a publicly released heat map (see photo). The heat map provided an overall summary of activity using Strava-based wearable devices between 2015 and 2017. There was no individual information provided in the map, although it is possible to narrow the focus using enough outside information about a person in limited instances.
Strava provided aggregate fitness tracker information in a publicly released map like this one of Bagram airfield in Afghanistan.
The impact of this release was uncovered by 20-year-old Nathan Ruser, who is studying international security at the Australian National University. Ruser is also employed by the Institute for United Conflict Analysts.
The problem arises from information that can be inferred from the maps such as routes taken by soldiers around military bases. It can also highlight security efforts around company campuses, government buildings, and just about any other place where operational security could be compromised by information like this.
Side channel attacks in computer systems infer information because of weaknesses in implementations and algorithms. The recent Spectre and Meltdown processor issues are prime examples of side channel attacks. These attacks have also been conducted by tracking RF and power deviations. This is why there are many approaches used to make crypto hardware tamper-resistant. The idea is to prevent attackers from discovering any useful information by observing the device or software.
Side channel computer attacks tend to be very focused, but the idea is the same: Attackers try to get information that they can use by looking at unintended consequences of normal operation.
I already mentioned wearable tech like the Strava fitness tracker, but this location type of information is applicable to devices that might be stationary, like smart speakers. Initially they did not identify the person or their location with respect to the speaker, but that is changing as the devices become more capable. They will be able to identify the person by their voice from any device, since they are all tied to the cloud. The cloud-based voice command systems also have to who, when, where and what is being discussed, essentially eavesdropping.
So, what do online development tools have to do with this? Well, one thing that Strava does is sell the aggregate data, often with a finer grain of detail, to people who use the system. It is all there in the click through release you need to use the product, but it is doubtful that 99.999% of the people who have clicked it understand the long-term implication of using the data. It can be used for useful purposes, such as city planning or health studies, but, as we have seen, it can be used for nefarious purposes as well.
The use of online development tools, or software in general, has been increasing significantly over the years. It provides a way for vendors to track users and what they are doing. Privacy and security are important to developers and their companies, plus most online contracts keep this in mind, but typically cloud service providers can “use anonymous aggregate data” any way they want. How would you like it if a competitor knew that your latest compiles were generating lots of errors?
The challenge with all these systems is that what is collected, how it is processed, and where the results of this processing wind up can be difficult to determine. There are significant advantages to using all these devices and services. Some are provided for “free” so that the providers can utilize any information they obtain for other purposes from trying to sell additional products or services, or possibly providing this information to third parties so they can do something with the information.
So beware that you are signing up for whether you are buying into a fitness tracker, a new computer, or an online service. There may be more to be concerned about than where you might be walking.
About the Author
William G. Wong
Senior Content Director - Electronic Design and Microwaves & RF
I am Editor of Electronic Design focusing on embedded, software, and systems. As Senior Content Director, I also manage Microwaves & RF and I work with a great team of editors to provide engineers, programmers, developers and technical managers with interesting and useful articles and videos on a regular basis. Check out our free newsletters to see the latest content.
You can send press releases for new products for possible coverage on the website. I am also interested in receiving contributed articles for publishing on our website. Use our template and send to me along with a signed release form.
Check out my blog, AltEmbedded on Electronic Design, as well as his latest articles on this site that are listed below.
You can visit my social media via these links:
- AltEmbedded on Electronic Design
- Bill Wong on Facebook
- @AltEmbedded on Twitter
- Bill Wong on LinkedIn
I earned a Bachelor of Electrical Engineering at the Georgia Institute of Technology and a Masters in Computer Science from Rutgers University. I still do a bit of programming using everything from C and C++ to Rust and Ada/SPARK. I do a bit of PHP programming for Drupal websites. I have posted a few Drupal modules.
I still get a hand on software and electronic hardware. Some of this can be found on our Kit Close-Up video series. You can also see me on many of our TechXchange Talk videos. I am interested in a range of projects from robotics to artificial intelligence.