It’s not difficult when reading about computer security to see a direct correspondence between the threats and countermeasures that physically exist in a military battle and today’s cyber equivalents. Instead of an elite Seal team stealthily directing air strikes on unsuspecting enemy positions, malware hidden in an email attachment can trigger the release of millions of financial records at a keystroke.
Indeed, as well as a common vocabulary, both types of attack and defense share a similar philosophy. A white paper1 about the role of ethical hacking includes a quote attributed to Sun Tzu, a 5th century BC Chinese general and the author of Art of War: “If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle.”
Nevertheless, using technology to create defensive advantages is a good way to tilt the playing field in your favor. A 2012 white paper2 discusses the relationship between operating system software and the host processor hardware from the viewpoint of security. By minimizing the amount of code running with the highest privilege level, fewer opportunities exist for errors. Compartmentalizing code and enforcing privilege rules among the four available levels—level 0 can call any other level, level 1 can only call levels 2 and 3, and level 2 can only call level 3—further eliminate infiltration routes for malware.
As the paper explains, a typical step taken by security-conscious companies is “… hardening the OS by removing unnecessary user accounts, eliminating unneeded services and system functions, and closing unnecessary ports.” Additional actions include keeping security vulnerability patches up to date and investing in “bodyguards” such as “… firewalls, intrusion detection and prevention systems, application firewalls, and anti-virus and anti-spam filters.”
If all these things have been done, your system will be much more robust but remains susceptible to attack—the risk has been reduced but not eliminated. Ethical hacking, also known as penetration or security testing, refers to the process of examining and challenging your own system’s defenses in the same way that a malicious hacker might do. Of course, the big difference is that when you find a weakness, you will correct it before it can be used against you. This is how many companies and large government organizations are learning about and reducing their vulnerabilities.
The hacking process
A good image to keep in mind is that of a medieval castle (Figure 1).This type of defensive structure provides several barriers between an external enemy and the enemy’s objective. The final goal can be as straightforward as annihilation but more often involves capture of something valuable. As Willie Sutton is claimed to have answered when asked why he robbed banks, “That’s where the money is.”1 The data being sought is inside the computer system being attacked.
Source: Jacqueline Macou, Pixabay
Reference 1 enumerates four distinct steps that occur in almost every hack attack and that are covered in detail in the Global Knowledge Training CEHv8 course:
- Reconnaissance
- Penetration
- Maintaining access and stealing data
- Covering tracks
Of these, penetration is the most important because it enables steps 3 and 4. Even if medieval armies couldn’t breach a castle’s curtain walls, they still had the option of tunneling underneath. One way or another, getting inside the defensive structure was necessary to gain the original objective or exact the most damage.
As a second choice, laying siege was a popular strategy—cutting off the castle and its defenders from any outside help eventually reduced food stocks to the point where surrender was the only option. At least that was the theory. There also are cases of the attackers giving up when their own lines of supply became disrupted. The modern denial of service (DOS) and distributed DOS equivalents certainly isolate the website being attacked and if sustained can have devastating economic effects.
Reconnaissance in the cyber sense involves learning as much as possible about the target environment. What can a hacker learn about the organization, its Internet presence, the company’s operations and personnel, and ideally, email addresses? Is there background material available on social networks?
An example in another white paper3 shows how this information can be used: “Incursion is often accomplished through the use of social engineering techniques, such as inducing unsuspecting employees to click on links or open attachments that appear to come from trusted partners or colleagues. Unlike the typical phishing attack, such techniques are often led by in-depth research on the target organization. In one case, a small number of human resource employees were targeted using an apparently innocuous attachment, a spreadsheet on hiring needs that appeared to come from a job listing website. In the case of Hydraq [an example of an advanced persistent threat (APT)], targeted users were led to a picture-hosting website where they were infected by a drive-by-download.” Symantec’s Advanced Threat Protection provides warning of known APTs.
Any weakness can be exposed by sufficiently persistent probing. Once inside a computer network, cyber attackers generally follow two routes: they either execute a “smash and grab” theft of data, or in more sophisticated intrusions, lie low and remain undetected while continuing to compromise the target enterprise’s data security. Step four—covering tracks—is one of the reasons that you often hear about an organization being hacked several years after the event: nobody discovered the hack until recently. Of course, once the trail goes cold, understanding the attack in detail and assigning blame become much more difficult.
Establishing a strong defense
If you can prevent step 2—penetration—you’re most of the way toward securing your computer system’s data. You can’t stop people performing step 1—reconnaissance—but you can limit the amount of information available to them. Of course, that means striking the right balance by including only what legitimate website visitors need and excluding superfluous material that could prove harmful.
How do you know that your defense is adequate? In Reference 2, this question is addressed by developing an inherently secure OS rather than by adding security features to an existing nonsecure one.
A genuinely secure OS
Beginning with the hardware, the reference states, “Unlike other microprocessors, [Intel’s] Itanium offers two hardware mechanisms to restrict access to individual memory pages. The first mechanism, hardware access rights, is used to provide read, write, and execute privileges to each memory page as a function of hardware privilege level…. The SourceT micro OS [from Secure64] employs this mechanism to establish the most restrictive possible hardware access rights for every image throughout the entire system…. The second mechanism, hardware protection keys, is unique to Itanium. These keys are independent of hardware privilege level and provide dynamic access control to specific memory pages. When needed, access to data can be granted only to the specific code that must access the pages…. A set of memory pages protected by a common protection key is called a ‘compartment.’”
A further hardware enhancement separates control data from program data by providing two separate stacks. As Reference 2 notes, the unique “RSE” stack, which is used to save and recall critical control values, “… resides in a compartment at a higher hardware privilege level than the code causing the RSE stores and loads, making it inaccessible to application code.” This doesn’t mean that buffer overflows can’t occur, but when they do, only application data will be corrupted, not the control information. In conventional buffer overflow attacks, carefully engineered code overwrites stack values, causing malicious execution to occur.
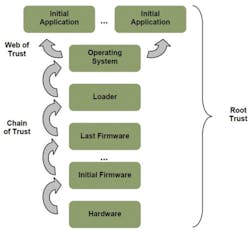
On the software side, Figure 2 depicts the “chain of trust” that is established by methodically authenticating the RSA digital signature of all code and data images on disk, layer by layer.
With permission from Secure64
Dealing with a conventional OS
Steps suggested when assessing vendor security are a good starting point. A white paper4 lists the System Administration, Networking, and Security Institute (SANS), the National Institute of Standards and Technology (NIST), and the Shared Assessment organization as three sources of industry-standard security assessment methodologies.
The paper continues with a list of 40 questions that you should ask potential suppliers when attempting to assess their cybersecurity preparedness. Grouping the questions with similar themes helps to identify several distinct types of activities:
- identification of critical assets;
- security personnel organization, experience, and performance;
- cybersecurity policy training, incident reporting, and recovery planning;
- vulnerability assessment—software, hardware, and third-party; and
- continuous monitoring.
The company sponsoring the white paper sells BitSight Security Ratings risk management software, so it’s not surprising that the paper closes by emphasizing the role of monitoring: “…You can’t possibly assess whether or not your vendor’s security is in order unless you have access to their network in real time. …If you use a continuous monitoring solution like BitSight [Technologies], you can take action against real threats immediately.” Nevertheless, it does have a valid point.
Monitoring communications activity is the best way to uncover a hacker’s exploit before it can gain traction. Has an unusual port been used for communication or has unexpected communication occurred? These are only two examples of the information that a security information and event management (SIEM) system provides. A three-part article5 about SIEM use notes, “… [a SIEM] must learn what’s normal in order to recognize what’s abnormal, because abnormal events are a strong indicator of an advanced threat or breach. It also has to be able to identify an attack pattern, even if it is spread out over a period of time.”
A SIEM system can correlate events to deduce nefarious activity. Successful logins at unusual times or from unusual locations, a string of several unsuccessful login attempts followed by a successful one, and attempts to access several parts of a system by using the same credentials are all signs of unusual events.
The second part of the article emphasizes the role of the SIEM operator: “…A robust understanding of normal log baselines and typical activities—which requires not just SIEM technology but also a skilled SIEM operator—will be extremely helpful…. In addition to deploying SIEM technology, collecting logs, running reports, and using correlation to trigger alerts, operational procedures need to be in place to have an effective server access monitoring process. For example, what happens when the systems administrator notices that the user logs in from two places at once?”
The final section of the article discusses the steps required to program the SIEM system to recognize attacks. The author questions, “If you were the attacker, how would you break in and steal the data? Model the attack and then enumerate that vector within the SIEM tool…. Launch the attack against yourself…. Then monitor what your SIEM does.” Correct the shortcomings and try again. Using this iterative approach, you will be able to establish a set of effective rules for that type of attack. Now you can move on to model and implement a solution for other types.
The article notes that the process is never done because your own system behavior changes over time as do both the types of attacks and the types of data that may be relevant to thwarting them. For example, network packet traffic monitoring may allow distinctive signatures to be developed and associated with certain types of attack.
What you’re up against
Certainly, there are fairly simple attacks occurring all the time—perhaps you have already been asked for your banking details by the Nigerian attorney handling a distant relative’s estate. However, increasingly, the threats facing Internet-connected systems are growing in sophistication.
The Hydraq Trojan that was active in the 2009-2010 time period could be introduced by opening an email attachment, but it also used a zero-day exploit for Internet Explorer—the so-called Aurora Exploit. Zero-day refers to a software bug that no one is aware of except the attacker. Hence, once that path is taken, the victim has zero days in which to defend against it.
Hydraq attempted obfuscation via spaghetti code, which makes the program flow hard to determine. Nevertheless, there are tools such as the Hex-rays decompiler that unjumble this type of code to reveal the distinct modules as human-readable higher-level text. This is essential so that the overall purpose can be determined. As described on the Hex-Rays website, “… high level language representation in Hex-Rays has several advantages:
- concise: requires less time to read it;
- structured: program logic is more obvious;
- dynamic: variable names and types can be changed on the fly; and
- familiar: no need to learn the assembly language.”
A Symantec Official Blog6 comments that spaghetti code was the only trick that Trojan.Hydraq used, making analysis relatively easy. However, as another Symantec document7 explains, this is not the case for Trojan.Clampi. In addition to a wide range of relatively common techniques such as heap spraying, encryption, encoding, and pattern matching via cyclic redundancy checking, “Clampi’s main executable and modules are protected with a commercial tool called VMProtect. This tool can be compared to runtime executable packers, for instance UPX and FSG, which decompress a file at runtime. Unlike common packers though, VMProtect does not only compress the target executable, but also virtualizes its code to render white-box analysis, if not impossible, extremely difficult to do.”
According to information on the VMProtect Software website, “The cornerstone principle of VMProtect is to provide efficient protection of the application code from examination by making the application code and logic very complex for further analysis and cracking. The main software code protection mechanisms VMProtect applies are virtualization, mutation, and combined protection that involves mutation of the application code with subsequent virtualization.”
The website further explains, “The crucial advantage of the virtualization method used in VMProtect is the fact that the virtual machine executing virtualized fragments of code is embedded into the resulting code of the protected application. Therefore, the app protected with VMProtect needs no third-party libraries or modules to function. VMProtect allows using several different virtual machines to protect different fragments of code of the same application resulting in even [a] more complicated cracking process, because a hacker now has to analyze [the] architecture of multiple virtual machines.”
Reference 7 concludes by commenting on the further difficulty that VMProtect adds to analysis: “Clampi’s main executable contains about 280 functions composed by more than 5,000 basic blocks, which can be time-consuming to reverse [engineer]…. Trojan.Clampi is an extremely versatile threat that is difficult to analyze and has the ability to update itself, replicate, and perform arbitrary actions at any time by downloading additional modules. Currently, the motivation behind Clampi is financial, and reports have linked Clampi to numerous stolen online banking credentials and the unauthorized transfer of funds.”
Conclusion
Unless your company is a large enterprise with valuable trade secrets or data, the company probably won’t be the target of an APT. Nevertheless, unless you continuously monitor your computer system, how will you know you’ve been hacked until well after the event?
If there are valuable assets at risk, perhaps a genuinely secure OS such as Secure64’s SourceT OS is appropriate. According to the company, genuinely secure OSs “… greatly reduce the risk to an organization by:
- eliminating the threat of malware and rootkits,
- maintaining system availability during a network attack, and
- storing and retaining sensitive information securely.
In addition to reducing risk, such systems also decrease operational costs by eliminating the need to:
- harden the operating system,
- perform emergency vulnerability patching, and
- recover from security breaches.”
References
- Withers, B., Hackers, Hacking, and CEHv8, Global Knowledge Training, White Paper, July 2014.
- Eliminating Malware and Rootkits, Secure64, White Paper, August, 2012.
- Advanced Persistent Threats: A Symantec Perspective, Symantec, White Paper, December 2011.
- 40 Questions You Should Have in Your Vendor Security Assessment, Bit sight Technologies, White Paper, November 2015.
- Corrigan, B. L., ed. “Making Your SIEM System the Best It Can Be,” scribd.com.
- Fitzgerald, P., “Seeing Past Trojan.Hydraq’s Obfuscation,” Symantec, Official Blog, Jan. 25, 2010.
- Falliere, N., et al, “Inside the Jaws of Trojan.Clampi,” Symantec, Security Response, November 2009.
For More Information
About the Author