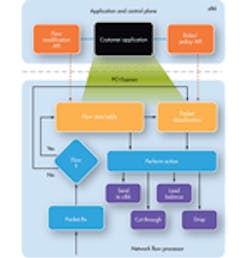
Packets hit key steps as they move through flow-processing engines used in applications that require 40 Gbits/s of stateful deep packet inspection, for example.
LF: What is flow processing?
JS: As the number of users on computing networks grows and the number of applications available to them explodes, it results in more individual conversations, or “flows,” on the network at any time. Flow processing is the ability for a communications application to keep active state on every individual network “conversation” traversing the device for the entire duration.
This includes every packet from beginning to end, as opposed to just individual packets. This state allows each packet in the flow to be treated the same way. The state that one might maintain on a flow could include flow length, duration, TCP state and sequence tracking, security policy to apply to the flow, and an action policy for the flow in question.
This “stateful” processing of network traffic requires managing large amounts of memory. It is a fundamental requirement for emerging networking applications and services such as stateful firewalls, intrusion detection systems, and quality-of-service enforcement platforms.
LF: What are the benefits of flow processing, and what types of applications require it?
JS: It is no longer sufficient to support today’s intelligent network and security applications with simplistic packet-by-packet traffic processing. Applications need to keep state on a per-flow basis to be effective. The benefits offered by stateful flow processing are numerous.
Flow processing allows for intelligent communication processing for a wide set of applications and services for plain-text and encrypted communications. The true benefits that flow processing provides are evidenced in the applications that the technology enables.
Maintaining the network state on all flows passing through a system is a critical requirement for security applications like virus scanning, firewalls, intrusion detection and prevention systems (IDS/IPS), distributed denial of service (DDOS) mitigation programs, data loss prevention (DLP) and test and measurement utilities, and network-forensics systems.
Rather than implementing simple packet-based processing, these types of applications require sophisticated security processing along with a high available instruction-per-packet rate and stateful management of flows at speeds 10 Gbits/s and higher. Without stateful flow processing, these applications could fundamentally not exist.
Other examples include the emergence of flow-based switches and routers. Forwarding of traffic based on flow as opposed to a per-packet basis allows switches and routers to more effectively support rate guarantees, control jitter and delay, and give application-based quality of service.
LF: What is the impetus for implementing it?
JS: There are numerous reasons why one would implement flow processing. The network is no longer about big pipes and plumbing. While high bandwidth and low latency will always be prerequisites for network evolutions, the amount of specialized content and security processing is where real demand comes from and is fueling growth.
Effective network security is an obvious driver for flow processing. As attacks become more sophisticated and attackers become better organized, IDS and IPS rely on flow processing to identify and stop attacks. These modern attacks use invasion techniques, such as spreading malicious traffic across packet boundaries, payloads, and even IP fragments, to avoid detection. These security systems must apply signature-based rules against the entire connection payload rather than simply examining traffic on a per-packet basis. This implies that the IDS/IPS keeps active flow state.
Another example is a stateful next-generation firewall. These devices retain significant attributes of each connection in memory, in which application identification and security processing happen at the beginning of the flow. The firewalls then use the flow state to process subsequent data in the session as a means of increasing performance.
LF: Where is flow processing deployed?
JS: Today, flow processing is deployed widely in a few specialized locations: enterprise and carrier data centers, enterprise perimeter, and carrier edge routers. It is rapidly moving to highly virtualized servers and to more and more line cards in general switching and routing infrastructure. At Netronome, we envision a day in the near future where every packet from every communication is intelligent and securely processed at every junction in the network infrastructure. The figure gives you some idea of the flow process as it deals with a packet during an application.
LF: How is it implemented?
JS: In theory, one could implement a flow processing system on any general-purpose processing architecture. But as network traffic and bandwidth increase, building these networks becomes an increasingly memory-intensive challenge. Processing huge volumes of traffic from millions of flows at high instruction rates requires large amounts of memory for state to be maintained across all of the packets in the flow.
Netronome delivers flow processing in processors that span a wide range of price, performance, and power envelopes, making them a part of enterprise-class and carrier-grade designs.
These flow processors use multiple techniques to provide more efficient memory-bandwidth usage than that of general-purpose processors. First, multiprocessing through as many as 40 independent networking- and security-optimized microengines can simultaneously process multiple independent streams of network traffic. Further, chip multithreading removes memory latency by allowing some processes to operate as other threads are waiting to complete.
LF: What Netronome products are now available to implement flow processing?
JS: The Netronome product line includes a family of ARM11-based network flow processors (NFP-32xx) and PCI Express acceleration cards that scale from 10 to 100 Gbits/s. They are used in carrier-grade and enterprise-class communications products that require deep packet inspection, flow analysis, content processing, virtualization, and security.
Netronome’s processors are powered by 40 programmable networking cores that deliver more than 56 billion instructions per second. This allows for over 1500 instructions and 50 flow operations per packet at 30 million packets per second, enabling 40 Gbits/s of L2-L7 processing with line-rate security and I/O virtualization for millions of simultaneous flows.
In addition, Netronome’s NFP technology is backward-compatible with the Intel IXP28XX processor, protecting customers’ immense investment in field-proven and network-hardened software. The NFP processors are also made available in easy-to-consume PCI Express acceleration cards with 1-, 10-, and 40-Gigabit Ethernet options. Netronome’s hardware offerings are supported by comprehensive development tools, production-ready software, and a broad ecosystem of premier partners and suppliers.
Netronome
www.netronome.com
About the Author

Lou Frenzel
Technical Contributing Editor
Lou Frenzel is a Contributing Technology Editor for Electronic Design Magazine where he writes articles and the blog Communique and other online material on the wireless, networking, and communications sectors. Lou interviews executives and engineers, attends conferences, and researches multiple areas. Lou has been writing in some capacity for ED since 2000.
Lou has 25+ years experience in the electronics industry as an engineer and manager. He has held VP level positions with Heathkit, McGraw Hill, and has 9 years of college teaching experience. Lou holds a bachelor’s degree from the University of Houston and a master’s degree from the University of Maryland. He is author of 28 books on computer and electronic subjects and lives in Bulverde, TX with his wife Joan. His website is www.loufrenzel.com.