GitLab’s DevSecOps Enhances Security for Software Developers
What you’ll learn:
- Looking at GitLab CI/CD under the hood.
- What “security built into the pipeline” actually means.
- How teams manage and act on findings at scale.
GitLab DevSecOps is an integrated system that unifies development, security, and operations within a single platform. Traditionally, software environments isolated those three and relied on separate tools, workflows, and teams.
Overcoming those issues, this comprehensive tool handles the full development lifecycle, from ideation and coding through testing, security checks, deployment, and monitoring. The end result is a seamless, automated process with security built in, enabling teams to release higher-quality projects more rapidly with fewer vulnerabilities.
DevSecOps embeds security into every development stage, rather than a separate review. Becauyse security functionality is implemented directly into the CI/CD (continuous integration/continuous deployment) pipeline, developers can code, apply changes, run automated tests, and receive security feedback in the same environment. This reduces friction by eliminating context-based handoffs that slow development when security checks occur late.
GitLab Runners
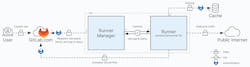
The CI/CD pipeline is powered by GitLab Runners. The lightweight, agent-like processes execute jobs defined in the .gitlab-ci.yml file (Fig. 1). Runners can be shared across multiple projects and are provided by GitLab in software-as-a-service (SaaS) environments. They execute pipeline jobs in isolated environments using virtual machines or containers, ensuring code execution doesn’t interfere with other jobs and maintains security boundaries.
Runners are compatible with advanced configuration for secure and efficient workflows. Jobs work with specific runners based on tags, operating systems, or container images. Teams can then isolate sensitive jobs like running secret detections or infrastructure-as-code scans. Caching and artifact storage allow results, test results, and security scan outputs to be preserved across pipeline stages, making security findings accessible.
Security Measures: SAST, DAST, Dependency and Container Scanning
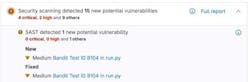
Static Application Security Testing (SAST) is one of the first ways GitLab integrates security into development (Fig. 2). SAST scans compiler libraries or analyzes source code to find potential vulnerabilities, including SQL injection, insecure function usage, or cross-site scripting.
This testing feature runs automatically after pipeline execution or a merge request creation, ensuring vulnerability detection before merging the code. Catching any known issues early is useful as developers can fix any problems while the code is fresh, reducing risk and remediation cost.
DevSecOps also uses dependency scanning. Applications typically have third-party libraries and packages in their build, and these can introduce vulnerabilities. To mitigate those issues, GitLab’s dependency scanning inspects packages and libraries during CI/CD, detecting insecure versions and flagging license compliance issues.
Scans run on all pipeline executions. Developers can then take action, addressing security alerts right away, which ensures vulnerable dependencies won’t make it into production unnoticed.
In addition, Dynamic Application Security Testing (DAST) works alongside static analysis. It inspects running applications for security flaws by simulating attacks in a runtime environment. This is an effective test as it finds vulnerabilities that manifest during application deployment, like misconfigured endpoints, authentication weaknesses, or improper input handling. Users can schedule DAST scans to run in pipelines, and these findings emerge with other security results for centralized tracking.
Organizations relying on containers can use container scanning to inspect Docker images for vulnerabilities in operating-system packages, base layers, and libraries. Integrating container scanning into the CI/CD pipeline allows GitLab to scan and verify all developed and deployed containers against security threats. This scanner runs after an image has been created or pushed, helping prevent known vulnerabilities from reaching production.
More Measures: Secret Detection, IaC Scanning Fuzz Testing
DevSecOps comes with secret detection as well. It ensures API keys, credentials, or other sensitive data aren’t committed to repositories. To prevent that from happening, GitLab automatically evaluates commits and the repository’s history for those secrets during pipelines. Once detected, the alerts appear in the merge request interface so that developers can remove any secrets before they’re seen externally.
Infrastructure-as-Code (IaC) scanning improves cloud-native deployment security by checking configurations like Terraform scripts, Helm charts, and Kubernetes manifests. GitLab evaluates those files for misconfigurations that may lead to exposed resources or privilege escalation. IaC scans run as part of pipelines or pre-deployment stages to ensure that infrastructure changes meet security practices before reaching development environments.
DevSecOps is compatible with Fuzz testing, an advanced security method that sends unexpected or malformed inputs to applications, revealing crashes, exceptions, or logic flaws. Fuzzing targets web interfaces, APIs, or backend services, unveiling small vulnerabilities that standard testing may not detect. Fuzz testing is implemented within the pipeline as a part of development instead of a separate security exercise, making it more likely to detect edge-case issues before release.
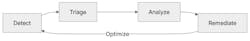
Apart from these scanning techniques, there’s a unified vulnerability management system (Fig. 3). All discoveries from SAST, DAST, dependency scanning, container scanning, secret detection, IaC, and fuzz testing are aggregated into a unified view. With this feature, teams can triage, prioritize, and track remediation, reducing duplicate alerts and provide an organization-wide view of risks. Keeping vulnerabilities in context ensures developers address the most important issues first.
AI Added to the Workflow
Recently, GitLab integrated Duo AI into DevSecOps, introducing artificial intelligence into the development workflow. Duo works like a context-aware assistant embedded into GitLab, delivering AI-powered suggestions, explanations, and automation. It also generates code, summarizes merge requests, produces tests, and offers guidance on vulnerabilities in real-time.
Instead of replacing traditional security or CI/CD tooling, Duo improves DevSecOps by helping developers understand and take action on security findings more efficiently, speeding up the remediation and review cycles. Duo allows security insights, code fixes, and testing recommendations to become more accessible. Doing so reduces delays and makes security part of the development process.
The Duo Agent Platform extends the AI’s role with multiple AI agents collaborating on various tasks within the DevSecOps lifecycle. Developers work with these agents to generate code, optimize CI/CD pipelines, analyze vulnerabilities, and assist with IaC configurations.
Coordinating AI within the platform enables the agents to have a more proactive, automated approach to security, testing, and deployment, making AI a participant in the workflow. This model ensures AI recommendations and interventions remain context-aware, project-specific, and integrated within GitLab’s compliance and governance frameworks.
These components —planning, coding, testing, securing, deploying, monitoring, and AI assistance —exist within a single platform, a strength of DevSecOps. Rather than navigating a toolchain, teams work within a unified ecosystem that maintains context, consistency, and clarity. This approach reduces operational overhead, improves developer productivity, and embeds security into the everyday workflows rather than treating it as a late-stage concern.
About the Author
Cabe Atwell
Technology Editor, Electronic Design
Cabe is a Technology Editor for Electronic Design.
Engineer, Machinist, Maker, Writer. A graduate Electrical Engineer actively plying his expertise in the industry and at his company, Gunhead. When not designing/building, he creates a steady torrent of projects and content in the media world. Many of his projects and articles are online at element14 & SolidSmack, industry-focused work at EETimes & EDN, and offbeat articles at Make Magazine. Currently, you can find him hosting webinars and contributing to Electronic Design and Machine Design.
Cabe is an electrical engineer, design consultant and author with 25 years’ experience. His most recent book is “Essential 555 IC: Design, Configure, and Create Clever Circuits”
Cabe writes the Engineering on Friday blog on Electronic Design.