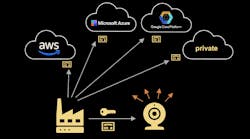
End-to-end security refers to starting at the factory, where chips are manufactured, through their use in the field in the Internet of Things (IoT). The trick is to have a secured chip or portion of a system-on-chip (SoC) with a secret key that’s the root of trust (ROT) for the entire system. Foundries are doing this now, but that’s only the beginning. The ROT and secure key storage can be used to securely link to cloud platforms like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform.
NXP Semiconductors’ solution is called EdgeLock 2Go, which initially supports the SE50 family of secure elements (Fig. 1). This ROT chip has secure key storage that can be used with the EdgeLock 2Go service. It starts when the chip is manufactured and is tied to the secure EdgeLock 2Go service.
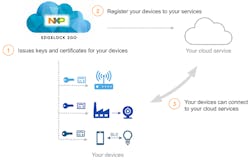
The next major step is the handoff to a cloud service (Fig. 2). This means adding secure keys that provide the encryption and authentication support for communication with the cloud service. Subsequently, applications on the cloud service can securely add keys to the chip, providing the basis for secure communication and enabling services on the IoT device. It also gives owners of a device management capability, and offers a way to transfer ownership from one device to another.
The basic service provided by EdgeLock 2Go is to link the chip, and effectively its device, to a cloud platform that then takes over management of the device. The “key” to this approach is that no encryption keys or digital certificates are handled by the OEM.
The collaboration between NXP and partners like AWS IOT and Microsoft Azure are already in place. It’s also possible to work with NXP to create a custom solution, but this will only be done with large customers that have the financial resources and need to go it on their own.
Standards and government organizations are starting to specify limits to the number of times a key can be used before it must be changed, so long-term management is part of the mix, too. Renewal and management are long-term issues, as many devices have a lifetime of a decade or more.