This file type includes high resolution graphics and schematics when applicable.
It’s been three months into your embedded development, and the engineering team just reported the security architecture design is complete. Hardware, operating system, algorithms, protocols, everything is ready to start developing—that is, until someone asks “How are we going to get keys into this thing?”
With no resources left to allocate, the answer is usually, “Well… that’s a manufacturing issue.” While this may satisfy the overworked development team, deferring infrastructure development jeopardizes the overall success and security of the product. Here are a few problems that can occur as a result:
• Lack of experience: Manufacturing personnel typically lacks the security experience required to implement the key management infrastructure required to produce secure embedded devices. This forces the hiring of specialized engineers or contractors, further driving up costs.
• Cutting corners: Manufacturing equipment and testing software are typically rolled into the per-unit cost of the product. Developing the infrastructure in the production phase reduces profit margins, causing engineers to cut corners under pressure to eliminate costs. This leads to poor implementation with scripts, poor random number generation, and improper key protection, causing susceptibility to cybersecurity attacks and unplanned costs.
• Complex supply chains = complex security: Today’s supply chains include in-house manufacturing, third-party contract manufacturers, strategic partners, and customers. Any number of keys must be shared with stakeholders in order to sign software and generate digital identities. With every copy of the keys, the risk of compromise grows exponentially.
All Internet of Things (IoT) industries are discussing end-to-end embedded security. According to a Gartner study, the number of IoT devices will grow to 26 billion units by 2020, a 30-fold increase from 0.9 billion in 2009. As the number of connected devices explodes, so does the need for built-in security. Malicious software running on other devices can collect network traffic and send false commands affecting reliability. Since it’s impossible to account for the security in other devices, product developers must design for confidentiality and authentication, which includes cryptographic algorithms and a security infrastructure.
To understand the importance of the security infrastructure and why it cannot be developed as an afterthought, we need to take a step back and understand the importance of keys in secure embedded systems.
The Importance of Keys
The goal of cryptosystem design is to minimize the risk and impact of a compromise. Symmetric algorithms are smaller, faster, and stronger per bit, but keys must be pre-placed between two endpoints. While global keys may be easier to manage, if one device is compromised, all devices are vulnerable to an attack.
The use of unique keys per endpoint minimizes the risk to other devices. Pre-placed keys are feasible in systems with few endpoints, and may be the only option in memory-constrained systems. However, the distribution and management of these keys becomes more complex with an increasing number of endpoints.
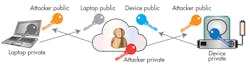
Asymmetric cryptography provides a path in systems with a large number of endpoints. Using asymmetric pairs, public keys are exchanged over the network to encrypt data and negotiate shared session keys for use with faster symmetric algorithms. While this allows us to create tunnels and encrypt data from point to point, the system is still vulnerable to the threat of a man-in-the-middle attack (Fig. 1).
A public key infrastructure (PKI) eliminates the man-in-middle threat by generating certificates and signed software to prove authenticity. These common infrastructure functions allow embedded systems to verify that software hasn’t been tampered with, and perform mutual-authentication of remote systems before exchanging data. Through PKI, systems are able to extend the root of trust from hardware to software and then to remote systems across untrusted networks.
Compromise of PKI keys impacts every device manufactured; and with access to the root key, an attacker can sign malicious software and create fake certificates. Attackers then have the ability to masquerade as valid systems, able to collect data and issue commands at will. When weighing the impact (one device versus all), protecting the root keys is the most critical function of the entire system and must be prioritized accordingly.
End-to-End Security Design
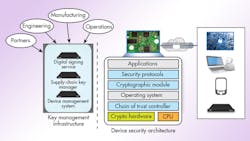
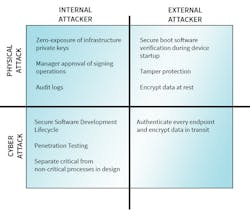
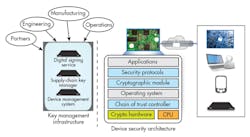
Developers need to prevent physical and network attacks by both external and internal attackers (Fig. 2). This is accomplished through a design that includes both the Device Security Architecture and Security Infrastructure (Fig. 3). An end-to-end security design addresses the protection of data and keys across all IoT product-lifecycle phases.
A Device Security Architecture typically includes:
• Chain of trust controller: Authenticates software and data prior to execution
• Operating Environment: Reliably control application execution and access to resources
• Cryptographic Module: Algorithm primitives and key storage
• Network Security Protocols: Authenticate and encrypt data to/from specific endpoints using cryptographic module algorithms
• Applications: Executes the intended function of the embedded system
The Enterprise Security Infrastructure incorporates:
• Digital signing service: Signs software and data for verification by the device
• Supply-chain key manager: Generates unique keys and certificates for each device during manufacturing and configuration
• Device Management System: Secure management and distribution of data, including software, commands, and control files, signed and/or encrypted per device
Enterprise Security Infrastructure
Leading companies are beginning to understand the importance of protecting root keys. The investment in device security hardware, cryptographic libraries, and protocols is realized through a key-management infrastructure. Therefore, securing the root keys is the cornerstone to embedded-system security. In response, industry leaders are now developing their key-management solutions first.
Due to the high number of stakeholders, building consensus for a robust in-house design can be an immeasurable task. Many companies do not have the engineering staff qualified to develop and maintain these systems to support a broad range of products. And those with security experience are still faced with developing firmware, database, interfaces, and reliability features. In addition to continued management, an infrastructure project is a significant undertaking for any organization.
Industry leaders understand that unlike production test stations, the key-management infrastructure needn’t be developed for each product. By developing the infrastructure solution first, organizations are able to incorporate use of the system into multiple products, thereby reducing per unit cost. An enterprise security infrastructure supports protection of multiple root keys in multiple locations as defined by the organization.
Companies have long standardized on hardware, software, and enterprise resource planning (ERP) systems to develop products better, faster, and cheaper. Today, with cyberattacks growing in both number and sophistication, security infrastructure is fast becoming an industry standard. By deploying an enterprise security infrastructure to support all of your embedded products, an end-to-end security design becomes possible.
About the Author
Gregory Rudy
Director of Business Development
Gregory Rudy, Director of Business Development, joined Green Hills Software - INTEGRITY Security Services in 2014 through the acquisition of Valicore Technologies. Mr. Rudy has over 15 years experience in the development of commercial and government technology. As systems architect at SafeNet Mykotronx, he led the development of several cryptographic solutions, including the first Type 1-certified tactical handheld and tablet computers. He holds a Bachelor of Science in Computer Engineering from Cal Poly, San Luis Obispo and Masters in Business from Johns Hopkins University.