Microchip and The Things Industries (TTI) are in cahoots together and they want to bring in developers to their secure circle. The idea is to provide secure authenticated communication as well as secure deployment.
The solution is built around Microchip’s ATECC608-MAHTN-T secure element chip (Fig. 1). This I2C device is a cryptographic coprocessor with hardware-based secure key storage. It can store up to 16 keys or certificates. It supports a range of encryption methods, including FIPS SP800-56A Elliptic Curve Diffie-Hellman (ECDH), NIST standard P256 elliptic curve, SHA-256 and HMAC hash with off-chip context save/restore, and AES-128 with support for encryption/decryption and Galois field multiply for GCM.
1. Microchip’s ATECC608A-MAHTN-T secure element incorporates factory-installed keys that support secure registration and authentication.
The standard ATECCC608 comes with no keys installed, but they’re included with the LoRa variant. This is designed to work with TTI’s LoRa network support. LoRaWAN is a low-speed, long-distance wireless network protocol used for the Internet of Things (IoT).
Typically, a user generates a public/private key pair for use in a public key infrastructure (PKI) and registers the public key with TTI. The private key is programmed into a LoRa device. Communication between the TTI servers on the internet and the device can be authenticated. The process is a bit involved and works for an individual developer, but this is too cumbersome when deploying hundreds to millions of devices.
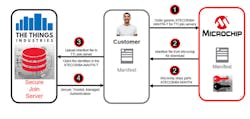
Working with TTI is one way to manage the process, and larger organizations could do this, but the two companies have made the process easy regardless of the number of devices a company plans to deliver. The secure key provisioning system starts with ATECC608A-MAHTN-T chips that are programmed at the factory with private keys that have a matching Manifest file containing the associated public key information (Fig. 2). The Manifest file is signed by Microchip and can be recognized by TTI when it receives the file. It then adds the key to its secure join server database. At this point, the device with the secure element can communicate securely with the secure join server.
2. A customer can order an ATECC608A-MAHTN-T (1). Microchip sends back a digitally signed Manifest file and the chip (2). Then the customer provides the file to TTI (3) so that the device can securely communicate with the secure join server (4).
The secure element will actually have a second private key because LoRa implements a dual security system. One is for the network and the other is for the service associated with the device. This allows for secure communication with the network and another internet-based server where the service can use distinct and independent authentication mechanisms. The additional key storage on the secure element is available for other application-dependent uses.
The private keys in the secure element are never revealed for any steps with the process. This is a key (pun intended) aspect of the approach. Microchip and TTI have private keys that are also never revealed. It prevents keys from being compromised at any point within the delivery of a LoRa solution.
The pre-provisioned solution comes with one year of TTI Join Server service. It also supports re-keying should a device need to migrate to another join server.
In addition, Microchip provides a LoRa protocol stack that supports the ATECC608A-MAHTN-T. The secure element can work with most any host capable of using the I2C interface.
The ATECCC608 is designed to defend against a range of attacks, including microprobing, timing attacks, emissions analysis, fault or invalid command attacks, and power cycling and clock glitches. There’s active shield over the entire chip and all memories are internally encrypted. Data-independent crypto execution is included, and the system uses randomized math operations. The system is designed with internal state consistency checking.
The chip uses voltage tampers and isolated power rails as well as an internal clock. Furthermore, Microchip applies secure test methods without using JTAG; no debug probe points or test pads are on the chip.
A company can also deploy its own secure join server. The same, pre-programmed secure element will work with either server. The ATECC608A has received a high Joint Interpretation Library (JIL) rating that’s defined by the Common Criteria security standard.
3. The ATECC608A can be placed into a AT88CKSCKTUDFN-XPRO module (right) and combine with a LoRaWAN radio (center) and host (left).
Microchip provides LoRa client hardware and software that’s compatible with this solution (Fig. 3). The secure element is used in a removable module (AT88CKSCKTUDFN-XPRO).
About the Author
William G. Wong
Senior Content Director - Electronic Design and Microwaves & RF
I am Editor of Electronic Design focusing on embedded, software, and systems. As Senior Content Director, I also manage Microwaves & RF and I work with a great team of editors to provide engineers, programmers, developers and technical managers with interesting and useful articles and videos on a regular basis. Check out our free newsletters to see the latest content.
You can send press releases for new products for possible coverage on the website. I am also interested in receiving contributed articles for publishing on our website. Use our template and send to me along with a signed release form.
Check out my blog, AltEmbedded on Electronic Design, as well as his latest articles on this site that are listed below.
You can visit my social media via these links:
- AltEmbedded on Electronic Design
- Bill Wong on Facebook
- @AltEmbedded on Twitter
- Bill Wong on LinkedIn
I earned a Bachelor of Electrical Engineering at the Georgia Institute of Technology and a Masters in Computer Science from Rutgers University. I still do a bit of programming using everything from C and C++ to Rust and Ada/SPARK. I do a bit of PHP programming for Drupal websites. I have posted a few Drupal modules.
I still get a hand on software and electronic hardware. Some of this can be found on our Kit Close-Up video series. You can also see me on many of our TechXchange Talk videos. I am interested in a range of projects from robotics to artificial intelligence.