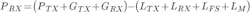The use of IoT to connect everyday devices has, in turn, created a massive ecosystem of wireless protocols, application-specific radio chips/modules, and prototyping/development boards. There are already nearly 9 billion IoT devices globally—a number that is anticipated to nearly triple to 25.4 billion by 2030. The massive array of these wirelessly-connected sensor networks all have with it varying payloads, data capacities, link distances, determinism, security, and latencies in varying topologies that can be point-to-point, point-to-multipoint, star or mesh, to best suit its respective IoT use case.
This article focuses on evaluation boards for implementing an industrial wireless connection for the far-reaching IoT nodes within a facility. A discussion on the considerations for these types of wireless nodes, as well as their applications, is considered in order to equip the reader with a better understanding of electrically and mechanically ruggedized IoT devices for high reliability wireless applications.
A Look at wireless protocols for high reliability IoT
There are many non-industry-specific IoT networks such as Zigbee, Z-wave, and 6LoWPAN that are often used in low-powered indoor mesh networks for home automation and general automation purposes. However, high reliability applications require a level of guaranteed determinism, security, scalability, and range for extendibility. Protocols that are specifically geared towards industrial applications such as WirelessHART and ISA10.11a potentially offer this with nominal data rates and relatively low-latency communications. However, there is less adoption of these technologies, as they are not as commonly used. There are therefore far less commercial options for the implementation of such IoT networks, and the lack of vendor diversity can drive up the cost, scalability, and potential continuity of supply when employing these solutions. Protocols such as Bluetooth, Bluetooth low energy (BLE), WiFi, and cellular-based IoT protocols such as NB-IoT and LTE-M already have a large operating base, due to the ubiquity of cellular networks. Newer, low power wide area networks (LPWANs) have filled a unique niche in connectivity by using the sub-GHz spectrum in combination with narrowband (NB) and ultra-narrowband (UNB) modulation schemes to achieve large link distances with low-powered devices. This allows distant nodes to be connected without the need for battery changes and maintenance. However, these networks are typically used in applications that require low payloads transmitting infrequently. For instance, for scheduled check-ins in oil pipelines to monitor the health of the pipeline via flow-rate measurements and seismic monitoring. Table 1 lists the basic differences between some of these wireless networks—this illuminates the slight fundamental differences between the various IoT protocols and how they can best serve their specific applications.
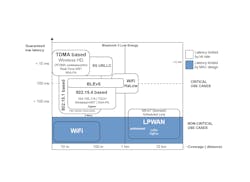
It is apparent that there is really no one-size-fits-all solution for all IoT applications. Figure 1 illuminates the link distance and latency of some IoT protocols—critical use cases require scheduled, low latency communications in order to ensure reliable monitoring/control of sensor/actuator nodes. However, there are other considerations for these wireless technologies, including their data rate, scalability (capacity), battery life, and security.
Reliable IoT communication for fringe IP devices
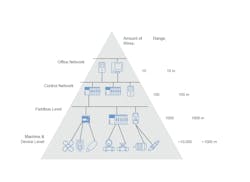
The typical industrial automation system hierarchy involves various communication levels that involve different requirements on the network (Figure 2). From the top down, this starts at the office level, control level, fieldbus level, down to the machine- and device-level. The node density increases exponentially toward the bottom of the hierarchy, where high capacity, mesh networks (e.g., WirelessHART, ISA 100.11a, WiFi HaLow, 6LoWPAN, etc) are often necessary in order to support the capacity requirements and allow for the centralized collection of data at the control level for potential use cases that involve machine learning (ML) and artificial intelligence (AI) such as predictive analytics and sensor fusion.
Benefits of replacing modest data rate WiFi installations with a secure, reliable ethernet-enabled connection
At the office and control network levels, ethernet-based radios have high utility for the ability to remotely configure a device regardless of the location of the control/office network. Moreover, ethernet interfaces are increasingly familiar in the industrial setting with industrial ethernet overtaking traditional fieldbus technologies for industrial controls and communications. A high throughput connection opens doors significantly for potential wireless applications, including commercial applications such as digital signage and secure retail point-of-sale (POS) systems and more industrial applications such as surveillance, robotics, industrial automation, and smart grid communications.
The IP addressability of devices has also become a significant concern for massive machine-type communications (mMTC) where there is a massive influx of devices where the option of incorporating a unique identifier becomes difficult to accomplish. However, this is a critical consideration for many industrial automation vendors1, the ability to tag devices with a global address enables its remote management where devices can be linked/delinked and data can be authorized/deauthorized remotely. Ethernet to RF modules enable the wireless connectivity of IP devices on a network without the wired ethernet connection. There is, however, the major consideration of link distance and security of the wireless connection. The encryption available in standard WiFi devices is often inadequate to protect against any malicious attack. Therefore more flexible industrial wireless ethernet-based solutions with custom coding can protect sensitive data for a more secure and reliable connection.
Potential use cases for securely connecting fringe IP devices
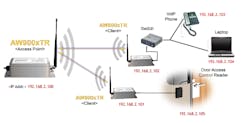
IoT applications can vary between indoor use cases within the plant floor with link distances of tens of meters, to outdoor applications connecting distant devices at tens of kilometers—sometimes with both indoor and outdoor devices connected on the same network. These each have with it respective link budget considerations. Industrial IoT and other high reliability applications including military, medical, and surveillance applications require securely connected devices with an ensured quality of service (QoS), and remote firmware upgrades to minimize the costs associated with node maintenance/repairs. Ethernet-to-RF modules can provide a robust and secure, wireless control for a mobile robot (Figure 3). These applications are increasing in usage for industrial applications with autonomous guided vehicles (AGV) and their respective vision systems utilizing navigation algorithms (e.g., simultaneous location and mapping (SLAM)) and various vision technologies (e.g., LiDAR) for movement in dynamic environments. This can also be seen with autonomous mobile robots (AMRs) for inventory transport, order picking, and sortation, allowing for cooperative human-machine interactions. These types of machines require a seamless, high throughput, low latency connection, regardless of environmental obstacles, in order to enable maximal control and responsiveness.
A government agency or private industry sectors (e.g., healthcare, energy, financial, etc) are often required to encrypt sensitive data with a method that conforms to the National Institute of Standards and Technology) NIST standard FIPS 140-2—a US government security standard that is leveraged to certify both the hardware and software components of cryptographic modules. This involves at least one approved algorithm/security function (e.g., 18 bit AES encryption) as well as either tamper-evident coatings/seals that make apparent any malicious tampering to obtain physical access to the plaintext cryptographic keys and critical security parameters (CSPs), or pick-resistant locks on covers or doors to the enclosure3. This type of standard for instance, applies to surveillance video, access control, and perimeter sensor communications at a secure facility. Other use cases include digital signatures for the banking industry or outdoor payment systems such as a fuel center.
Prototyping a secure wireless system for reliable communications
Constraints around the link budget become increasingly important when attempting to replace previous WiFi and other medium- to high-throughput IoT systems that were rendered ineffective due to insufficient range or excessive interference. As shown in Equation 1, link budget relies on a number of critical parameters.
In this equation, PRX/PTX is the power received and transmitted, GTX/GRX is the gain of the transmit/receive antennas, LTX/LRX is the loss of the transmitter/receiver, LFS is the free space loss, and LM are the miscellaneous losses (e.g., fading, multipath, foliage, wall penetration, etc). In order to optimize the power received, the power transmitted must be optimized as well as the gain of both the transmit and receive antennas. The benefit of leveraging the unlicensed band (e.g., 900 MHz, 2.4 GHz, 5 GHz) is the cost-effectiveness of not requiring an FCC license to operate or install nodes. However, there is the additional consideration of FCC regulations on the equivalent, isotropically radiated power (EIRP)—the maximum amount of power radiated from an antenna considering both antenna gain and transmitter power. In order to maximize the link budget it is important to achieve the maximum legal radiated power, this allows for orders of magnitude greater range than traditional WiFi devices.
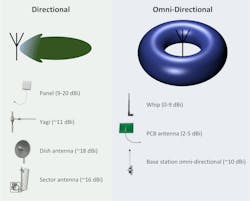
Antenna gain can be maximized over a point-to-point link between directional antennas as the bulk of the electromagnetic energy is positioned on the main lobe. This diverges from the traditionally leveraged omnidirectional, whip antenna that allows for nominal gain over 360 degrees on the horizontal plane. Vertical beamwidths can vary between 10° and 50°. Omni-directional antennas are ideal for mesh topologies with point-to-multipoint network where nodes are located in relatively close proximity to each other.
Considerations when troubleshooting a wireless system with evaluation boards
While there are some basic hardware considerations to take into account in order to maximize the reliability of a link. It is also important that the evaluation board utilized can illuminate potential failure modes and help mitigate them. Modules with the ethernet to wireless connectivity allows for plug-and-play capabilities with native IP devices such as laptops, door access control readers, and VoIP phones. On the other hand, modules with high speed SPI or UART interfaces will more readily connect to sensors for a WSN instead of readily connecting native IP devices. Some development platforms come with a custom web browser interface to manage remote diagnostics, monitoring, and link analysis (Figure 7)—this is typically acquired through a vendor with a customized GUI. Features such as link analysis can be accomplished via a built-in spectrum analyzer that would readily identify interference issues while monitoring. For some development kits compliance and certification is critically important, especially when utilizing established protocols such as Bluetooth or modules with cellular connectivity. When using the unlicensed spectrum, however, the most critical design consideration is typically conforming to FCC EIRP regulations. Ethernet-based nodes can both readily connect to each other as well as the cloud for the centralized integration of collected data. More often than not, firmware updates are required after the first release of an IoT network as well as periodically in order to upgrade and futureproof the native system. Remote firmware upgrades typically require a relatively high throughput connection, making them less viable for battery-constrained devices such as those in LPWAN installations. However, ethernet-to-RF modules can accomplish this without the need for a multi-radio platform supporting multiple low and medium throughput IoT protocols (e.g., LoRa+WiFi, sub-GHz+BLE, etc.). For outdoor environments, additional ruggedization is often required. This can be accomplished via weatherproof enclosures with lightning protection to buffer sensitive internal circuitry from power surges.
Securing your wireless IoT network
There are many aspects to ensuring the reliability of an IoT network. This includes the security/encryption algorithms utilized, tamper-proof considerations protecting keys, a high enough data rate to encourage remote firmware upgrades and more remote monitoring options, as well as ensuring the hardware is optimal in characteristics, location, and environmental protection. This level of ruggedization is not typical to most well-known IoT applications (e.g., home automation, smart city, etc). However, it is necessary for many private sectors including specific industrial applications, finance, and medical use cases. This includes the secure connection of wireless IP devices in geographically distant locations on the plant-floor or a secure facility.
References
- https://www.isa.org/intech-home/2017/september-october/features/expanding-opportunities-for-industrial-iot
- Seferagić, Amina et al. “Survey on Wireless Technology Trade-Offs for the Industrial Internet of Things.” Sensors (Basel, Switzerland) vol. 20,2 488. 15 Jan. 2020, doi:10.3390/s20020488
- https://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.140-2.pdf
About the Author
Tinu Oza
Product Manager, L-com
Tinu Oza is the IoT Product Manager at L-com and has been involved in the wireless and telecommunications industry for over 30 years, including extensive work in the areas of wireless antenna and device product development. He currently oversees the development of L-com’s growing line of IoT sensor products, which include ready-to-ship pressure and level sensors.