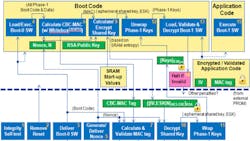
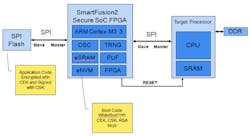
Microsemi is putting its SmartFusion 2 (see Secure Gen 2 Cortex-M3 Flash FPGA Prevents Counterfeiting) in between the boot ROM (usually an SPI flash device) and the host processor to provide a more robust, secure boot environment (Fig. 1). The flash memory contains encrypted code that the SmartFusion system can verify and decode. The host runs a boot program that verifies system operation and then continues the boot process.
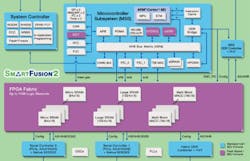
The SmartFusion platform is a flash-based FPGA built around an ARM Cortex-M3 microprocessor (see FPGA Combines Hard-Core Cortex-M3 And Analog Peripherals). The SmartFusion 2 (Fig. 2) concentrates on the digital side and drops the analog engine found still available in the first version.
Related Articles
- Secure Gen 2 Cortex-M3 Flash FPGA Prevents Counterfeiting
- FPGA Combines Hard-Core Cortex-M3 And Analog Peripherals
- Innovative Integration Mixes Micros WIth FPGAs
- Climb On Board Next-Generation FPGAs
The SmartFusion 2's secure boot support does not require the FPGA support allowing designers to provide additional functionality
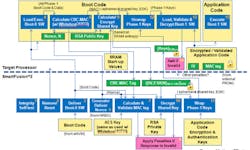
The full boot process (Fig. 3) is rather extensive and it verifies all aspects of the system from the SmartFusion chip itself to the boot code and the host. The end result of a successful boot is a host running a secure kernel that can then load an operating system and applications that have also been verified. The secure host boot application will have the keys necessary to do this.
The multistep process is necessary to address the various areas of attack. The chip itself is tamper-resistant and it has the secure keys to get everything started. The conventional SPI flash contains encrypted code that cannot be subverted. The host will eventually be running verified code that can then determine whether the subsequent operating system is authentic before running it. A secure operating system can then verify and load applications in a similar fashion. This might even make use of secure, encrypted disk storage.
Without the root trust, there is no way to protect the system. SmartFusion 2 uses differential power analysis (DPA) resistant anti-tamper measures licensed from Cryptography Research Incorporated (CRI).
There is a new SmartFusion 2 reference design that secures each stage of the boot process. It works with Microsemi's WhiteboxCRYPTO security product. This enables transport of symmetric encryption key in a plain text environment through complex algebraic decomposition of the crypto key and strong obfuscation. Microsemi also provides a graphical user interface for encrypting the developer's application code for subsequent programming of the SPI flash as well as the decryption in the host processor.
About the Author
William G. Wong
Senior Content Director - Electronic Design and Microwaves & RF
I am Editor of Electronic Design focusing on embedded, software, and systems. As Senior Content Director, I also manage Microwaves & RF and I work with a great team of editors to provide engineers, programmers, developers and technical managers with interesting and useful articles and videos on a regular basis. Check out our free newsletters to see the latest content.
You can send press releases for new products for possible coverage on the website. I am also interested in receiving contributed articles for publishing on our website. Use our template and send to me along with a signed release form.
Check out my blog, AltEmbedded on Electronic Design, as well as his latest articles on this site that are listed below.
You can visit my social media via these links:
- AltEmbedded on Electronic Design
- Bill Wong on Facebook
- @AltEmbedded on Twitter
- Bill Wong on LinkedIn
I earned a Bachelor of Electrical Engineering at the Georgia Institute of Technology and a Masters in Computer Science from Rutgers University. I still do a bit of programming using everything from C and C++ to Rust and Ada/SPARK. I do a bit of PHP programming for Drupal websites. I have posted a few Drupal modules.
I still get a hand on software and electronic hardware. Some of this can be found on our Kit Close-Up video series. You can also see me on many of our TechXchange Talk videos. I am interested in a range of projects from robotics to artificial intelligence.