This article is part of the TechXchange: Cybersecurity
Between ransomware attacks and requests for backdoors, it is not a good time for privacy and security these days. It is getting harder to protect yourself, your company, and your products as the wave called the Internet of Things (IoT) comes rushing toward us. In general, we are going to have to make do with the best we can in a very bad situation.
Some of the latest issues included the FBI’s request of Apple, and others, for a backdoor into their products. I really hate backdoors because they effectively bypass the security of the system and effectively eliminate that security. It goes back to the weakest-link syndrome. At this point, Apple and others are resisting government attempts to incorporate backdoors into systems.
Backdoors are also a problem because they tend to be implemented poorly, making them easy targets. The really bad ones use standard interfaces and hardwired user names and passwords. Backdoors also tend to be hidden in various ways, from obscuring the code to using non-standard ports and protocols. Although not directly related to backdoors, root kits are often installed by a virus or worm via a backdoor. Root kits essentially prevent subsequent detection. There are extreme cases like some hacks found in hard-drive controllers that have an infected operating system that cannot be deleted (see “Hacking Hard Drives and Other Nasties”).
Backdoors or conventional virus attacks are the likely cause of Hollywood Presbyterian Medical Center being locked out for 10 days by ransomware before they paid a $17K ransom in Bitcoins (see “Hospital pays $17k for ransomware crypto key”). Ransomware is where an attacker demands payment to remove the attacking software. As with any ransom, there is always the risk that the attacker is not “honorable” and will or can remove the system corruption.
Part of the issue for network-wide attacks, especially for hospitals and industrial systems, is that much of the hardware and software was never designed for hardened security environments. Operating systems like Windows XP are still found on these systems because getting updates is costly, often requiring recertification that is even more costly. Few organizations will put firewalls or other protections between these devices and their network, assuming that their network firewalls are sufficient. They are not.
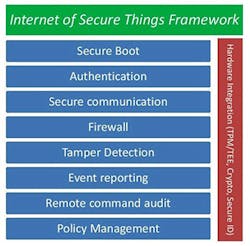
Alan Grau from Icon Labs has written articles for us highlighting the types of features needed in a secure environment (see figure). Cybersecurity is doable, but it requires up-front design and detailed implementations (see “What is Really Happening in the World of Cybersecurity?” on electronicdesign.com). The underlying design philosophy is security in depth as a single layer, like a simple firewall, can usually be broken, leaving the resulting system open to attack.
I do have to mention another related issue, locking down systems. This is common on smartphones and a recent FCC directive is being taken by some vendors as a reason to lock down products like WiFi access points and routers (see “Write the FCC Now! Save Wi-Fi” on electronicdesign.com). In this case, remote updates can only be done using vendor-supplied software. This tends not to be an issue for most users, but there are two related instances where this becomes a problem.
The first is simply those users that want to replace the software with an alternative. In the case of WiFi routers, open-source software like DD-WRT and OpenWRT provides features often lacking in vendor-supplied software.
The second is a matter of having to turn to those open-source alternatives because the vendors refuses to fix security issues. There are literally thousands, if not millions, of products on the market that have major security problems that will never be fixed by the vendors, some of whom may no longer be in business. Many of those products are still in use. This is not limited to WiFi routers. Everything from medical equipment to smartphones to cars are subject to this problem.
Unfortunately there are no simple answers, but I do have some recommendations. Do not allow backdoors of any kind. Demand access to and use of strong encryption. Ask vendors to provide a mechanism for user-controlled updates. The latter is not going to be easy, but it is something worth looking into. Consider that the latest UEFI-based computer systems typically support secure booting where the user can select the operating system to be used. This is typically Windows or Linux, but at least there are alternatives.
For myself, I would really like a standard for devices to report to a local security management device. This would track both the operation of the devices as well as provide a way to check for updates and security issues. At this point such a useful system is beyond even a determined sysadmin.
Here is hoping that you never get hit by ransomware or a virus but the odds of this happening to you are going up.